Before you throw your computer into a lake, rest ensured this ain’t over. In the days, weeks, and periods to follow honestly, indeed in the next few hours the...
Search Results For - Privacy
The maker of a sneaky adware that hijacks a user’s browser to serve ads is back with a new, more advanced version — one that can gain root...
That’s frequently the case with net impartiality: a handful of Republican delegates have joined their voices to those demanding the FCC to delay the vote that...
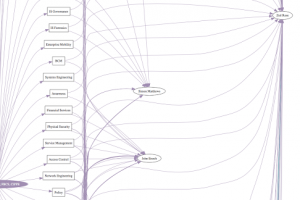
An OSINT tool that allows you to draw out relationships between people on LinkedIn via endorsements/skills. Check out the example (digraph), which is based on...
Similar to questionable stingray devices, DRT’s operations nicknamed “dirt boxes” mimic cellphone pillars, relating to every smartphone within a specific area...
When ironed about how Yahoo failed to realize that 3 billion accounts and not 500 million as first proclaimed were endangered in what was later revealed to be...
Security GNU/Linux distribution designed with cloud pentesting and IoT security in mind. It includes a full portable laboratory for security and digital...
Apple’s privacy signs do not spread to the thousands of app developers who will gain access to facial data in order to increase entertainment features for...
Are you a proud iPhone owner? If yes, this could freak you up. Trust me! Your iPhone has a serious privacy concern that allows iOS app developers to take your...
Canvas fingerprinting relies on websites meaning able to receive data from HTML canvas details calmly. In future, Firefox users will be required to give their...