[sc name=”ad_1″] If your computer has been infected with PyLocky Ransomware and you are searching for a free ransomware decryption tool to unlock...
Search Results For - Phishing
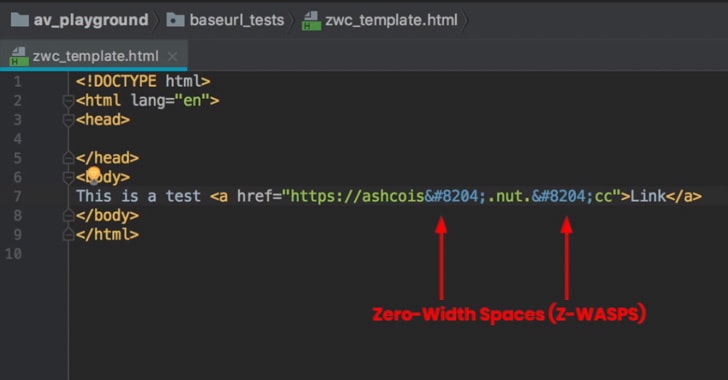
[sc name=”ad_1″] Security researchers have been warning about a simple technique that cybercriminals and email scammers are already being using in...
[sc name=”ad_1″] The real identity of Tessa88—the notorious hacker tied to several high-profile cyber attacks including the LinkedIn, DropBox and...
[sc name=”ad_1″] Cybersecurity researchers have discovered a new zero-day vulnerability in Adobe Flash Player that hackers are actively exploiting...
Tested on Kali Linux. Should work with all Debian based distros (and other ones if you have the right packages installed) BabySploit is a penetration testing...
Mass mailer is commonly used to send a phishing page link to the e-mail ID of the target. The attacker needs to be aware of the e-mail harvester technique to...
FIDO U2F Security key is a personal encryption method which individualizes your online security by providing a secondary layer of encryption via the USB port...
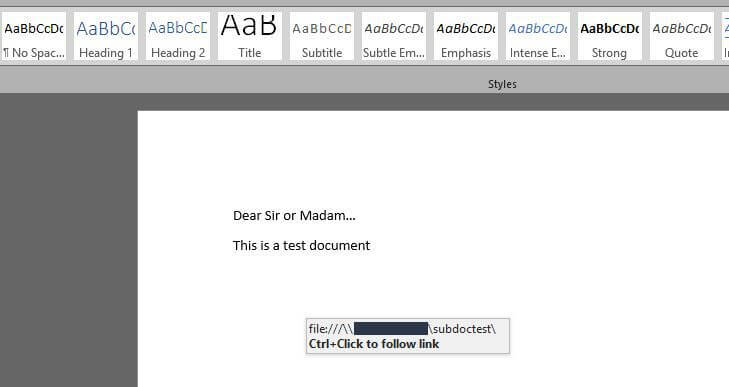
Security researchers from Rhino Labs (a US-based cyber-security firm) have found that cyber criminals can use a Microsoft Word feature dubbed subDoc to fool...
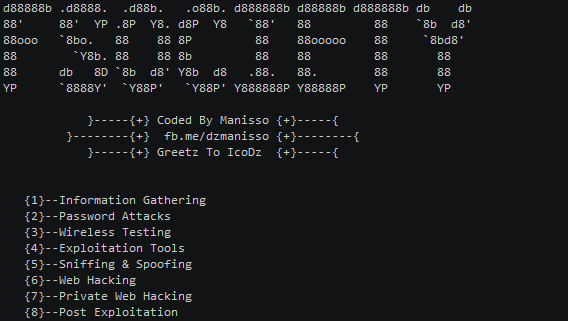
A Penetration Testing Framework , you will have every script that a hacker needs Menu Information Gathering Password Attacks Wireless Testing Exploitation...
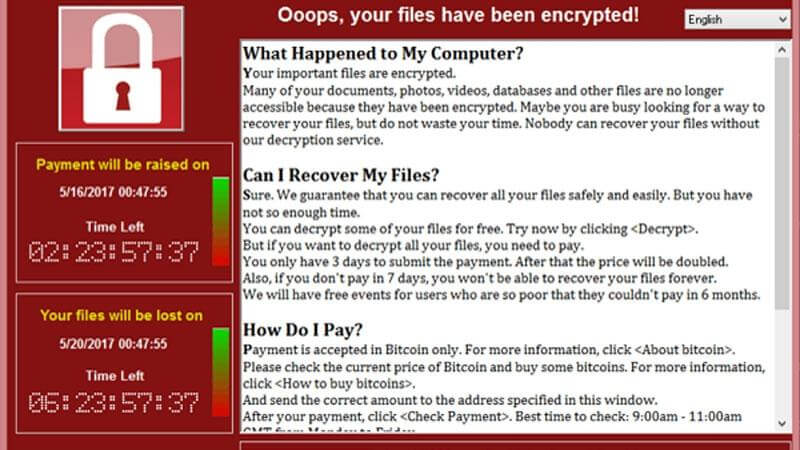
North Korea says there is no evidence to back the US claim it was behind the WannaCry ransomware attack. The US was “unreasonably accusing the DPRK...