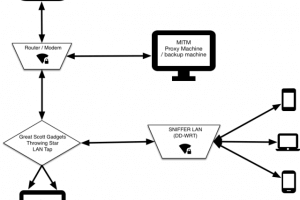
Essentially it’s a WiFi hotspot that is continually collecting all the packets transmitted across it. All connected clients’ HTTPS communications are subjected...
Search Results For - Packet
Network Security Monitoring (NSM) is, put simply, monitoring your network for security related events. It might be proactive, when used to identify...
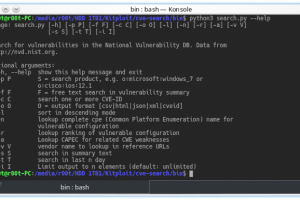
cve-search is a tool to import CVE (Common Vulnerabilities and Exposures) and CPE (Common Platform Enumeration) into a MongoDB to facilitate search and...
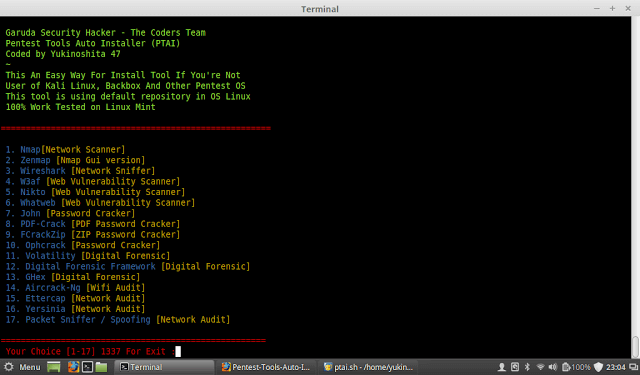
A Simple tool for installing pentest tools and forensic tools on Debian / Ubuntu Based OS Tested on Linux Mint And Kali Linux How To Do ?? Change Your...
Security researchers have discovered several key management vulnerabilities in the core of Wi-Fi Protected Access II (WPA2) protocol that could allow an...
cve-search is a tool to import CVE (Common Vulnerabilities and Exposures) and CPE (Common Platform Enumeration) into a MongoDB to facilitate search and...
The Port Scan Attack Detector psad is a lightweight system daemon written in is designed to work with Linux iptables/ip6tables/firewalld firewalling code to...
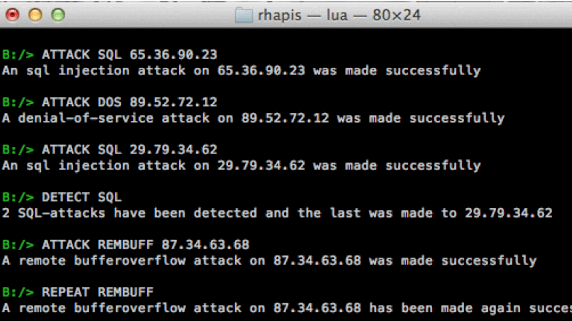
Network intrusion detection systems simulator. RHAPIS provides a simulation environment through which user is able to execute any IDS operation. Basic Usage...
Portia aims to automate a number of techniques commonly performed on internal network penetration tests after a low privileged account has been compromised...
Habu is to teach (and learn) some concepts about Python and Network Hacking. These are basic functions that help with some tasks for Ethical Hacking and...