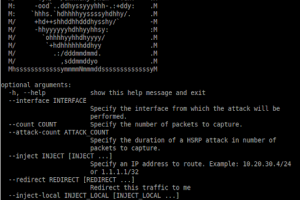
[sc name=”ad_1″] Routopsy is a toolkit built to attack often overlooked networking protocols. Routopsy currently supports attacks against Dynamic...
Search Results For - Networking
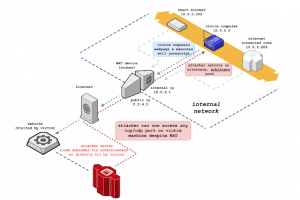
[sc name=”ad_1″] NAT Slipstreaming allows an attacker to remotely access any TCP/UDP services bound to a victim machine, bypassing the...
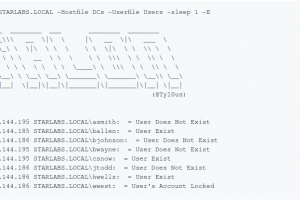
[sc name=”ad_1″] Talon is a tool designed to perform automated password guessing attacks while remaining undetected. Talon can enumerate a list of...
[sc name=”ad_1″] NFCGate is an Android application meant to capture, analyze, or modify NFC traffic. It can be used as a researching tool to...
[sc name=”ad_1″] ezEmu enables users to test adversary behaviors via various execution techniques. Sort of like an “offensive framework for...
[sc name=”ad_1″] SecGen creates vulnerable virtual machines, lab environments, and hacking challenges, so students can learn security penetration...
[sc name=”ad_1″] Terminal and Web console for Kubernetes Features Configuration from kubeconfig files (KUBECONFIG environment variable or $HOME/...
[sc name=”ad_1″] Docker for pentest is an image with the more used tools to create an pentest environment easily and quickly. Features OS...
[sc name=”ad_1″] The Forerunner library is a fast, lightweight, and extensible networking library created to aid in the development of robust...
[sc name=”ad_1″] Shellerator is a simple command-line tool aimed to help pentesters quickly generate one-liner reverse/bind shells in multiple...