A security researcher has discovered several critical vulnerabilities in one of the most popular embedded real-time operating systems—called FreeRTOS—and its...
Search Results For - Memory
The best gaming laptops and the best laptops were almost indistinguishable, few years ago. As long as you had an Intel Core i7 processor, 8GB of RAM and...
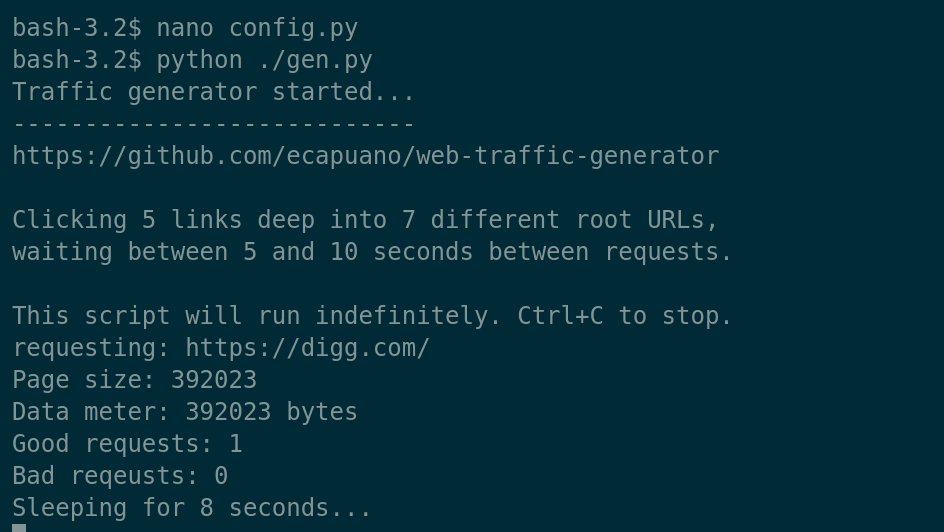
Just a simple (poorly written) Python script that aimlessly “browses” the internet by starting at pre-defined rootURLs and randomly...
Nameles provides an easy to deploy, scalable IVT detection and filtering solution that is proven to detect at a high level of accuracy ad fraud and other types...
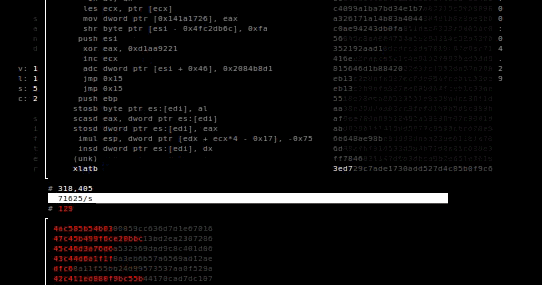
The sandsifter audits x86 processors for hidden instructions and hardware bugs, by systematically generating machine code to search through a processor’s...
A framework based on the Fiddler web debugger to study Exploit Kits, malvertising and malicious traffic in general. Installation Download and install the...
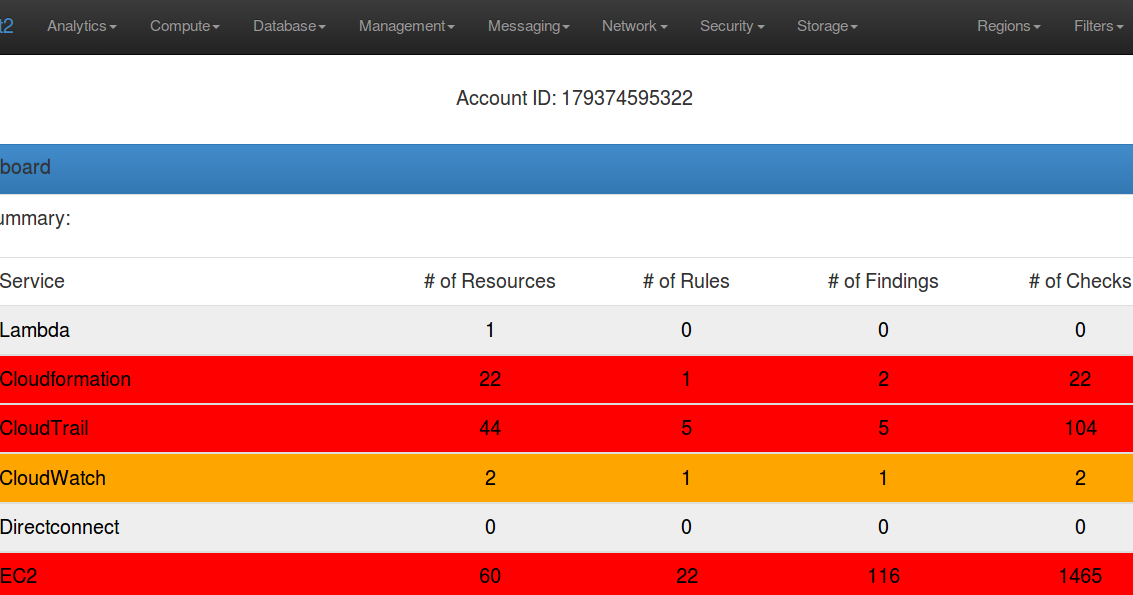
Scout2 is a security tool that lets AWS administrators assess their environment’s security posture. Using the AWS API, Scout2 gathers configuration data...
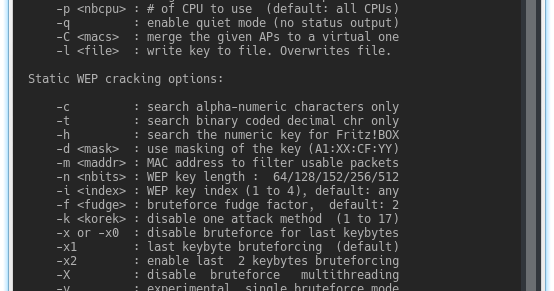
Aircrack-ng is a complete suite of tools to assess WiFi network security. It focuses on different areas of WiFi security: Monitoring: Packet capture and export...
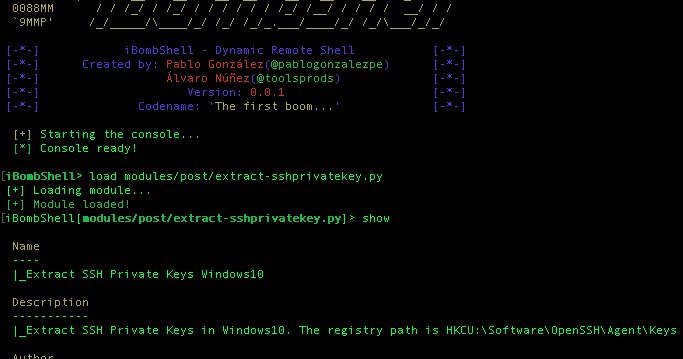
ibombshell is a tool written in Powershell that allows you to have a prompt at any time with post-exploitation functionalities (and in some cases exploitation)...
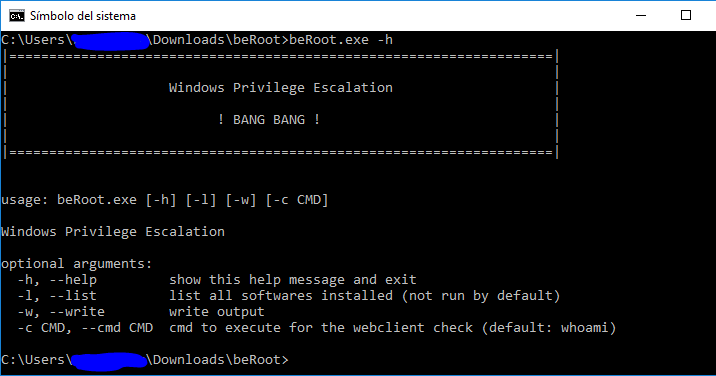
BeRoot(s) is a post exploitation tool to check common Windows misconfigurations to find a way to escalate our privilege. A compiled version is available here...