ACLight is a tool for discovering privileged accounts through advanced ACLs (Access Lists) analysis. It includes the discovery of Shadow Admins in the scanned...
Search Results For - Memory
What if I told you that there is a method will let you execute commands on Microsoft Word without any Macros, or memory corruption?! This Macro-less code...
Reverse Engineer .NET Assemblies dnSpy is a tool to reverse engineer .NET assemblies. It includes a decompiler, a debugger and an assembly editor (and more)...
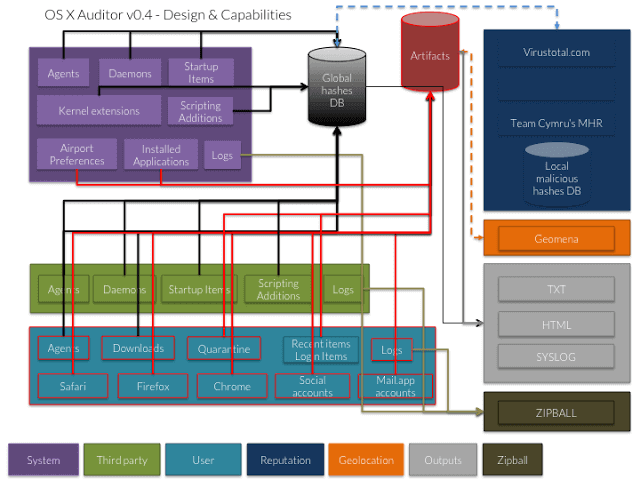
OS X Auditor is a free Mac OS X computer forensics tool. OS X Auditor parses and hashes the following artifacts on the running system or a copy of a system you...
objection is a runtime mobile exploration toolkit, powered by Frida. It was built with the aim of helping assess mobile applications and their security posture...
If you are an iPhone user and use Uber app, you would be surprised to know that widely popular ride-hailing app can record your screen secretly. Security...
It seems sophisticated hackers have changed the way they conduct targeted cyber operations—instead of investing in zero-days and developing their malware; some...
BitCracker is the first open source BitLocker password cracking tool. BitLocker is a full-disk encryption feature available in recent Windows versions (Vista...
Nameles provides an easy to deploy, scalable IVT detection and filtering solution that is proven to detect at a high level of accuracy ad fraud and other types...