The official blog of jQuery—most popular JavaScript library used by millions of websites—has been hacked by some unknown hackers, using the pseudonym...
Search Results For - Management
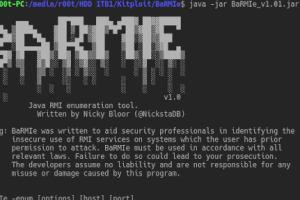
BaRMIe is a tool for enumerating and attacking Java RMI (Remote Method Invocation) services. RMI services often expose dangerous functionality without adequate...
Security researchers have discovered several key management vulnerabilities in the core of Wi-Fi Protected Access II (WPA2) protocol that could allow an...
Shadow is a unique discrete-event network simulator that runs real applications like Tor and Bitcoin, and distributed systems of thousands of nodes on a single...
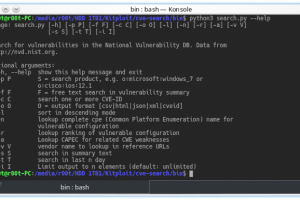
cve-search is a tool to import CVE (Common Vulnerabilities and Exposures) and CPE (Common Platform Enumeration) into a MongoDB to facilitate search and...
Belati is tool for Collecting Public Data & Public Document from Website and other service for OSINT purpose. This tools is inspired by Foca and Datasploit...
The Qatar administration also told internet users that they would be reviewing the issue though no decision or official comment on the blocks themselves have...
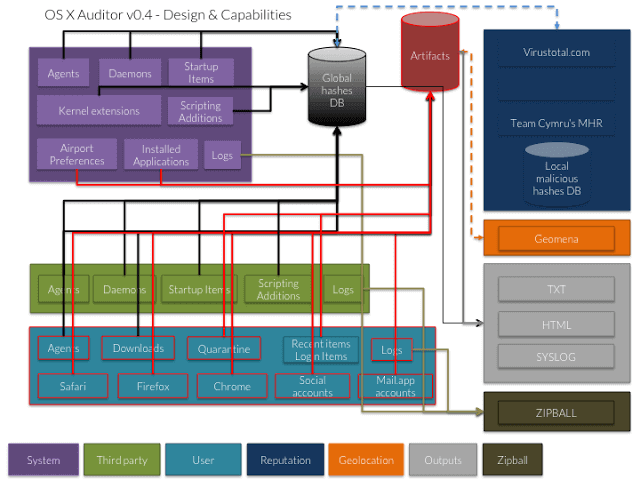
OS X Auditor is a free Mac OS X computer forensics tool. OS X Auditor parses and hashes the following artifacts on the running system or a copy of a system you...
It’s a pretty simple trade model, actually. They assume as much data about you from lenders, aggregate it, and sell it back to them,” said Brett Horn, an...
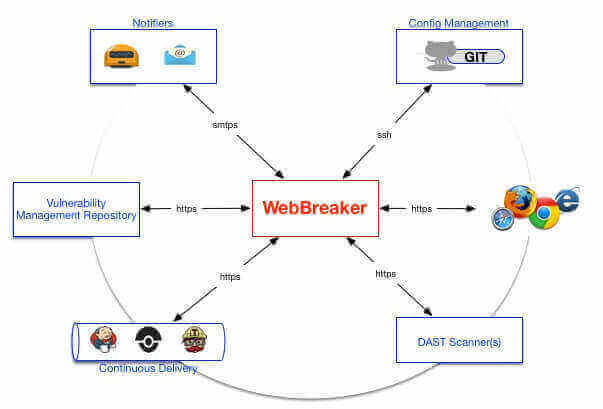
Build functional security testing, into your software development and release cycles! WebBreaker provides the capabilities to automate and centrally manage...