A former National Security Agency hacker has admitted to illegally taking highly classified information from the agency’s headquarters, which was later...
Search Results For - Malware
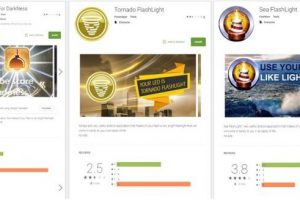
Google made many efforts to make the Play Store away from malicious apps, but some apps were able to fool the anti-malware protections and infect users with...
Security researchers have discovered a new, sophisticated form of malware based on the notorious Zeus banking Trojan that steals more than just bank account...
The GOSINT framework is a project used for collecting, processing, and exporting high quality indicators of compromise (IOCs). GOSINT allows a security analyst...
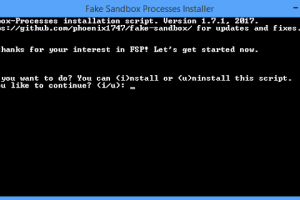
This small script will simulate fake processes of analysis, sandbox and/or VM software that some malware will try to avoid. You can download the original...
The Firefox sandboxing innovation confines the browser from the operating system in a way to block web attacks from using a vulnerability in the browser engine...
Just over a month after OnePlus was caught collecting personally identifiable information on its users, the Chinese smartphone company has been found leaving a...
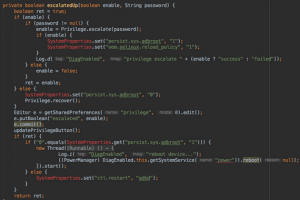
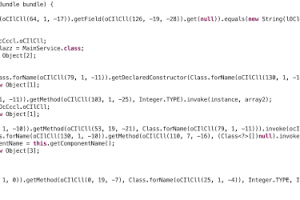
A pattern based Dalvik deobfuscator which uses limited execution to improve semantic analysis. Also, the inspiration for another Android deobfuscator: Simplify...
The tool itself is impressive enough, serving as the backbone of the CIA’s malware processes, but there’s more. What’s interesting about the first leak in the...
Security firm Positive Technologies lists being able to execute unsigned code on computers working the IME through USB. The fully fleshed-out details of the...