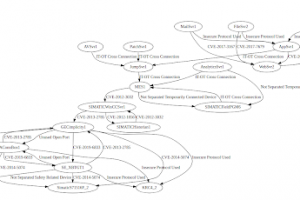
[sc name=”ad_1″] This prototype identifies security risk sources (i.e., threats and vulnerabilities) and types of attack consequences based on...
Search Results For - Logs
[sc name=”ad_1″] An organizational asset and vulnerability management tool, with Jira integration, designed for generating application security...
[sc name=”ad_1″] We at OpenEDR believe in creating a cybersecurity platform with its source code openly available to public, where products and...
[sc name=”ad_1″] teler is an real-time intrusion detection and threat alert based on web log that runs in a terminal with resources that we collect...
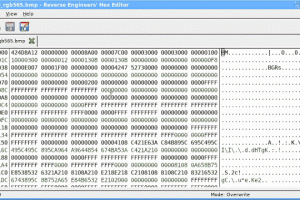
[sc name=”ad_1″] A cross-platform (Windows, Linux, Mac) hex editor for reverse engineering, and everything else. Features Large (1TB+) file support...
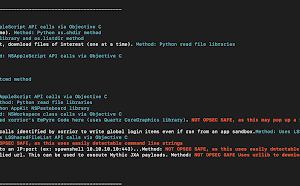
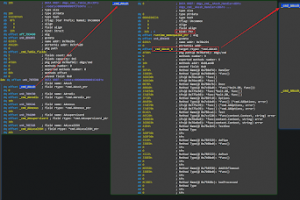
[sc name=”ad_1″] MacC2 is a macOS post exploitation tool written in python that uses Objective C calls or python libraries as opposed to command...
[sc name=”ad_1″] An automation tool that scans sub-domains, sub-domain takeover and then filters out xss, ssti, ssrf and more injection point...
[sc name=”ad_1″] Yet Another Golang Binary Parser For IDAPro NOTE: This master branch is written in Python2 for IDAPython, and tested only on IDA7...
[sc name=”ad_1″] Process Herpaderping is a method of obscuring the intentions of a process by modifying the content on disk after the image has...
[sc name=”ad_1″] tfsec uses static analysis of your terraform templates to spot potential security issues. Now with terraform v0.12+ support...