[sc name=”ad_1″] Without practice, theory is dead. Applied knowledge is essential in any area, especially in cybersecurity, and practice is the...
Search Results For - Logs
[sc name=”ad_1″] (CVE-2018-13379) Exploitation Tool, You can use this tool to check the vulnerability in your FortiGate SSL-VPN. ...
[sc name=”ad_1″] Damn Vulnerable Bank Android Application aims to provide an interface for everyone to get a detailed understanding with internals...
[sc name=”ad_1″] nginx Docker image secure by default. Avoid the hassle of following security best practices each time you need a web server or...
[sc name=”ad_1″] wsb-detect enables you to detect if you are running in Windows Sandbox (“WSB”). The sandbox is used by Windows...
[sc name=”ad_1″] An interactive command prompt that executes commands through proxychains and automatically logs them on a Cobalt Strike team...
[sc name=”ad_1″] Directed Greybox Fuzzing (DGF) like AFLGo aims to perform stress testing on pre-selected potentially vulnerable target locations...
[sc name=”ad_1″] Xerror is an automated penetration tool , which will helps security professionals and non professionals to automate their...
[sc name=”ad_1″] ToothPicker is an in-process, coverage-guided fuzzer for iOS. It was developed to specifically targets iOS’s Bluetooth...
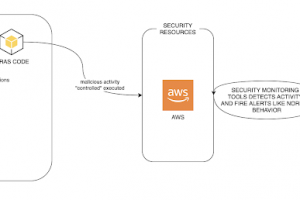
[sc name=”ad_1″] Security Incident Response Automated Simulations (SIRAS) are internal/controlled actions that provide a structured opportunity to...