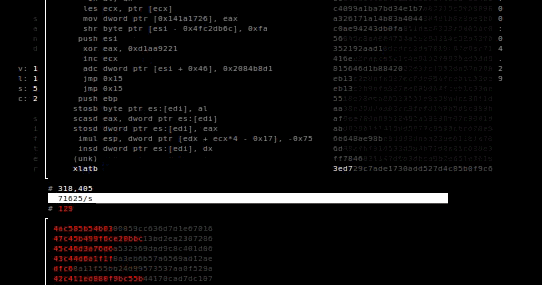
The sandsifter audits x86 processors for hidden instructions and hardware bugs, by systematically generating machine code to search through a processor’s...
Search Results For - Logs
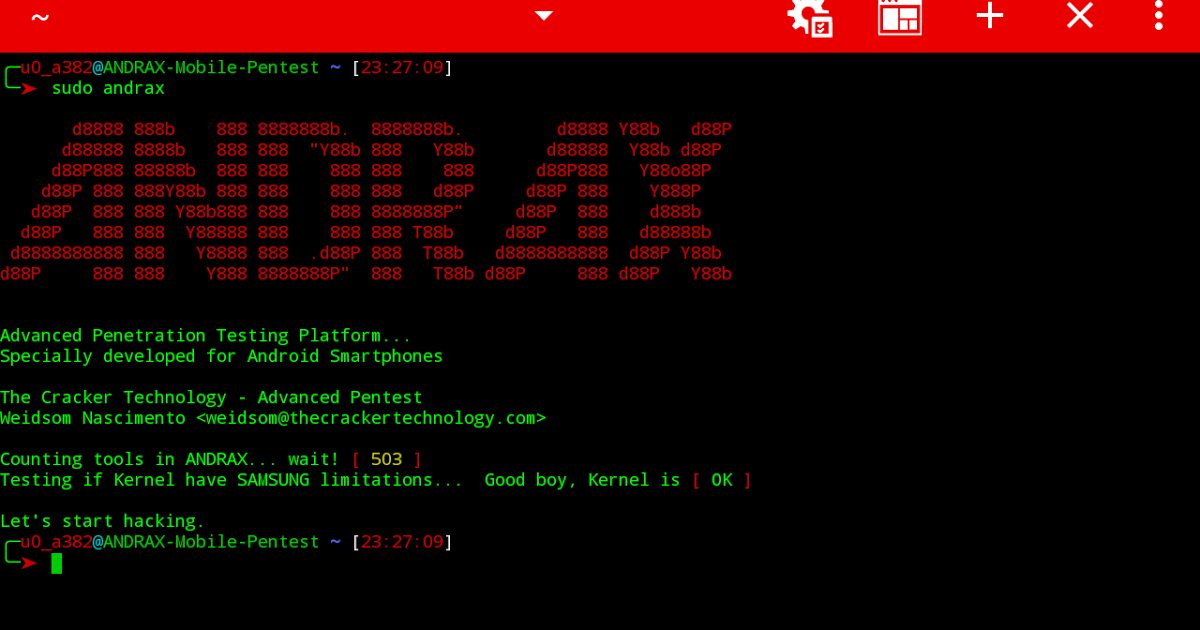
ANDRAX The first and unique Penetration Testing platform for Android smartphones What is ANDRAX ANDRAX is a penetration testing platform developed specifically...
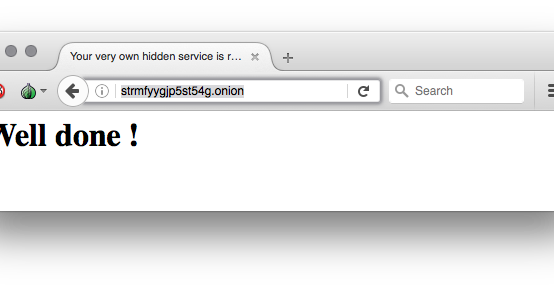
Easily run a hidden service inside the Tor network with this container Generate the skeleton configuration for you hidden service, replace for your hidden...
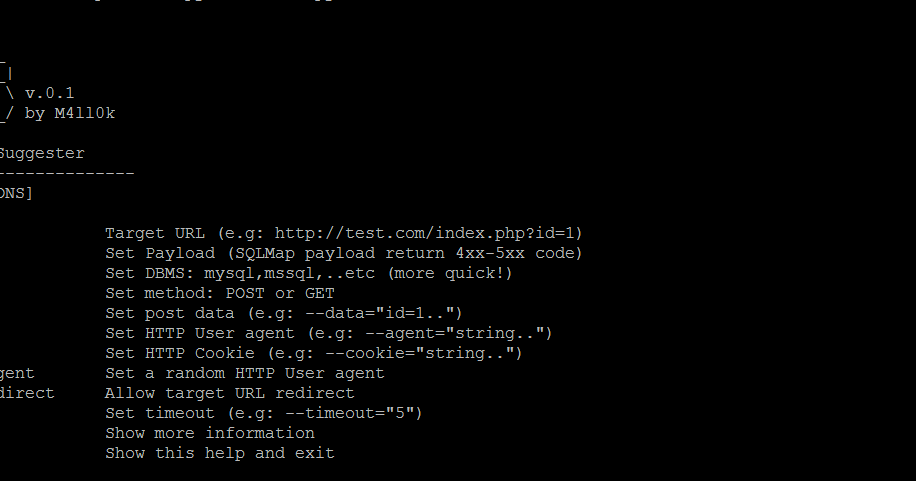
Atlas is an open source tool that can suggest sqlmap tampers to bypass WAF/IDS/IPS, the tool is based on returned status code. Screen Installation $ git clone...
A post-exploitation agent powered by Python, IronPython, C#/.NET. Requirements Server requires Python >= 3.7 SILENTTRINITY C# implant requires .NET >= 4...
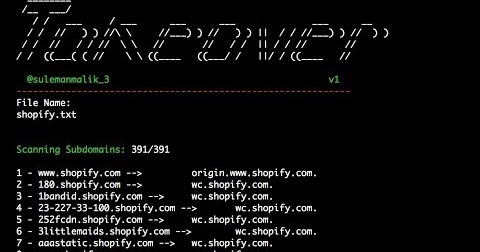
What is Subdomain Takeover? Subdomain takeover is a class of vulnerability where subdomain points to an external service that has been deleted. The external...
A framework based on the Fiddler web debugger to study Exploit Kits, malvertising and malicious traffic in general. Installation Download and install the...
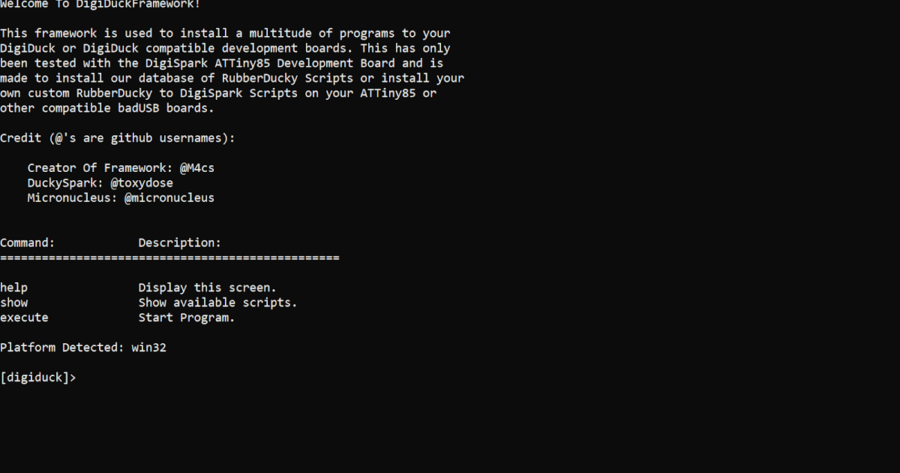
Framework for Digiduck Development Boards running ATTiny85 processors and micronucleus bootloader! Roadmap: Plan to implement a command for Duckyspark...
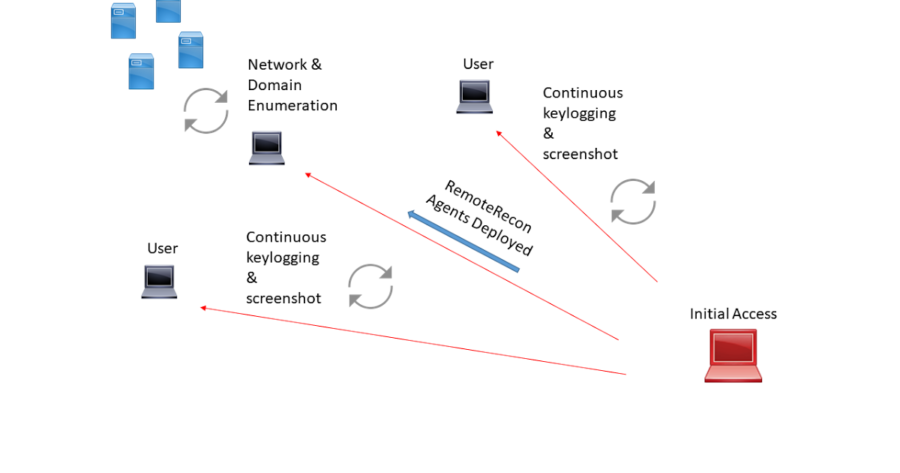
RemoteRecon provides the ability to execute post-exploitation capabilities against a remote host, without having to expose your complete toolkit/agent. Often...
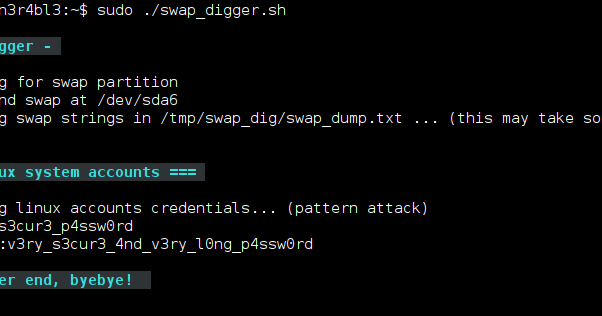
swap_digger is a bash script used to automate Linux swap analysis for post-exploitation or forensics purpose. It automates swap extraction and searches for...