[sc name=”ad_1″] BSF provides a discrete simulation environment to implement and extend peer-to-peer botnets, tweak their settings and allow...
Search Results For - Logs
[sc name=”ad_1″] Undetectable Reverse shell & Xor encrypting with custom KEY(FUD Metasploit Rat) bypass Top Antivirus like...
[sc name=”ad_1″] Espionage is a network packet sniffer that intercepts large amounts of data being passed through an interface. The tool allows...
[sc name=”ad_1″] Spyse is a cybersecurity search engine for finding technical information about different internet entities, business data, and...
[sc name=”ad_1″] A Misconfiguration Scanner cors misconfiguration scanner tool based on golang with speed and precision in mind ! Misconfiguration...
[sc name=”ad_1″] There are many scenarios where you would want to recover deleted data from your Mac. These deleted files could be your important...
[sc name=”ad_1″] A security testing tool to facilitate GraphQL technology security auditing efforts. InQL can be used as a stand-alone script or as...
[sc name=”ad_1″] SGN is a polymorphic binary encoder for offensive security purposes such as generating statically undetecable binary payloads. It...
[sc name=”ad_1″] TeaBreak is a simple burp extension for security researchers and bug bounty hunters for helping them to increase their work...
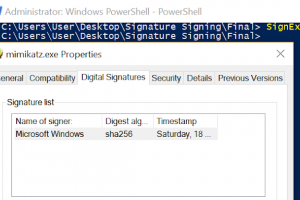
[sc name=”ad_1″] Hijacking legitimate digital signatures is a technique that can be used during red team assessments in order to sign PowerShell...