[sc name=”ad_1″] Safety checks your installed dependencies for known security vulnerabilities. By default it uses the open Python vulnerability...
Search Results For - Logs
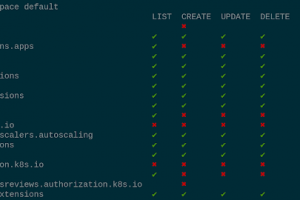
[sc name=”ad_1″] Review Access – kubectl plugin to show an access matrix for server resources Intro Have you ever wondered what access rights...
[sc name=”ad_1″] Resource monitor that shows usage and stats for processor, memory, disks, network and processes. Python port of bashtop. Features...
[sc name=”ad_1″] Browsertunnel is a tool for exfiltrating data from the browser using the DNS protocol. It achieves this by abusing dns-prefetch, a...
[sc name=”ad_1″] A Fuzzer For OpenRedirect Issues. Key Features : Takes a url or list of urls and fuzzes them for Open redirect issues You can...
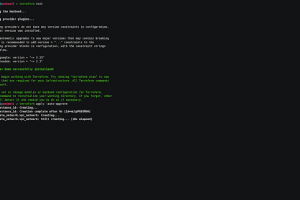
[sc name=”ad_1″] Create a VPS on Google Cloud Platform or Digital Ocean easily with the docker for pentest included to launch the assessment to the...
[sc name=”ad_1″] There are better ways than managing vulnerabilities with spreadsheets, especially when you are working with several tools. We know...
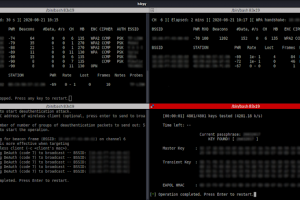
[sc name=”ad_1″] h4rpy is an automated WPA/WPA2 PSK attack tool, wrapper of aircrack-ng framework. h4rpy provides clean interface for automated...
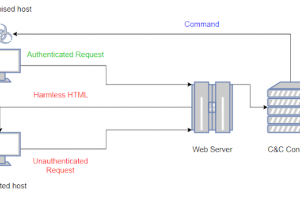
[sc name=”ad_1″] SNIcat is a proof of concept tool that performs data exfiltration, utilizing a covert channel method via. Server Name Indication...
[sc name=”ad_1″] LOLBITS is a C2 framework that uses Microsoft’s Background Intelligent Transfer Service (BITS) to establish the...