[sc name=”ad_1″] h2cSmuggler smuggles HTTP traffic past insecure edge-server proxy_pass configurations by establishing HTTP/2 cleartext (h2c)...
Search Results For - Logs
[sc name=”ad_1″] Polypyus learns to locate functions in raw binaries by extracting known functions from similar binaries. Thus, it is a firmware...
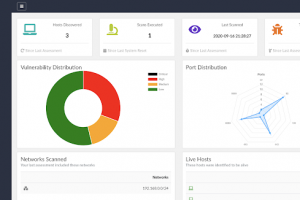
[sc name=”ad_1″] NERVE is a vulnerability scanner tailored to find low-hanging fruit level vulnerabilities, in specific application configurations...
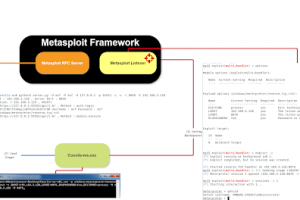
[sc name=”ad_1″] Cooolis-ms is a server that supports Metasploit Framework RPC. It is used to work for Shellcode and PE loader, bypassing the...
[sc name=”ad_1″] PwnedPasswordsChecker is a tool that checks if the hash of a known password (in SHA1 or NTLM format) is present in the list of I...
[sc name=”ad_1″] A project to get a Linux shell running on iOS, using usermode x86 emulation and syscall translation. For the current status of the...
[sc name=”ad_1″] Welcome to the Microsoft Defender Advanced Threat Protection PowerShell module! This module is a collection of easy-to-use cmdlets...
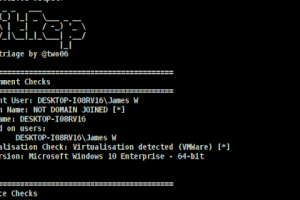
[sc name=”ad_1″] SitRep is intended to provide a lightweight, extensible host triage alternative. Checks are loaded dynamically at runtime from...
[sc name=”ad_1″] GRAT2 is a Command and Control (C2) tool written in python3 and the client in .NET 4.0. The main idea came from Georgios Koumettou...
[sc name=”ad_1″] What IS Moriarty? Advanced Information Gathering And Osint Tool Moriarty is a tool that tries to find good information about the...