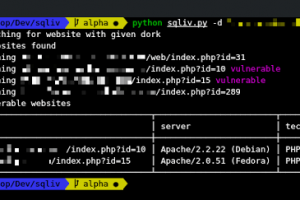
Massive SQL injection vulnerability scanner. Features multiple domain scanning with SQL injection dork by Bing, Google, or Yahoo targetted scanning by...
Search Results For - Linux
Exploit Pack has been designed by an experienced team of software developers and exploit writers to automate processes so penetration testers can focus on...
A wrapper tool for shadowsocks to consistently bypass firewalls. Quick start Automatically connect The easiest way to run this tool is just type ssct in...
Bash script purposed for system enumeration, vulnerability identification and privilege escalation. MIDA Multitool draws functionality from several of my...
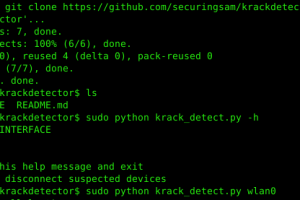
KRACK Detector is a Python script to detect possible KRACK attacks against client devices on your network. The script is meant to be run on the Access Point...
Security researchers have discovered several key management vulnerabilities in the core of Wi-Fi Protected Access II (WPA2) protocol that could allow an...
Ever been wondering if your ISP is hijacking your DNS traffic? Ever observed any misbehavior with your DNS responses? Ever been redirected to wrong address and...
Shadow is a unique discrete-event network simulator that runs real applications like Tor and Bitcoin, and distributed systems of thousands of nodes on a single...
Multi-platform transparent client-side encryption of your files in the cloud. Cryptomator provides transparent, client-side encryption for your cloud. Protect...
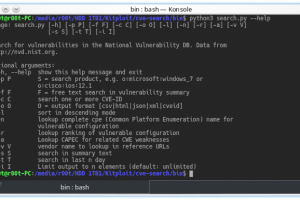
cve-search is a tool to import CVE (Common Vulnerabilities and Exposures) and CPE (Common Platform Enumeration) into a MongoDB to facilitate search and...