A security researcher (@s1guza) has published the details of an unpatched vulnerability in macOS that can be exploited to gain full control of a system. The...
Search Results For - Kernel
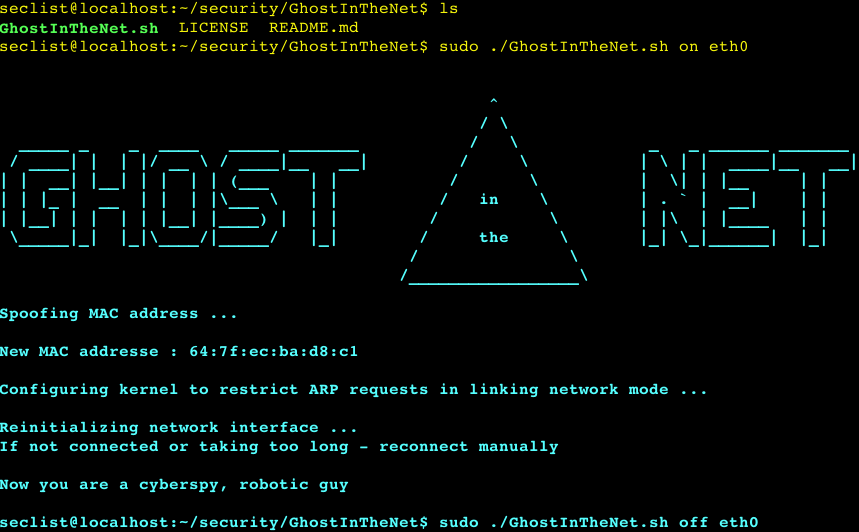
Ultimate Network Stealther that makes Linux a Ghost In The Net and protects from MITM/DOS/scan. Properties: Network Invisibility Network Anonymity Protects...
Security GNU/Linux distribution designed with cloud pentesting and IoT security in mind. It includes a full portable laboratory for security and digital...
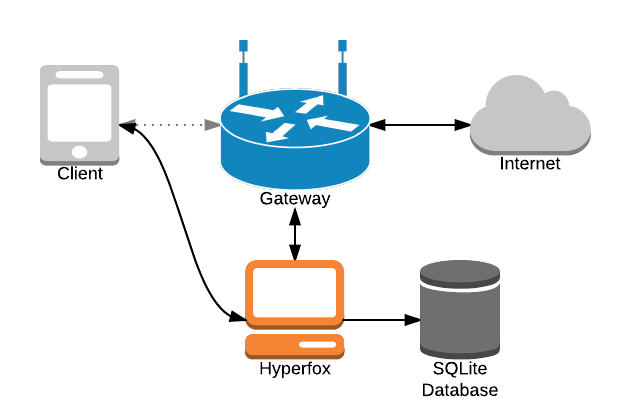
Hyperfox is a security tool for proxying and recording HTTP and HTTPs communications on a LAN. Hyperfox is capable of forging SSL certificates on the fly if...
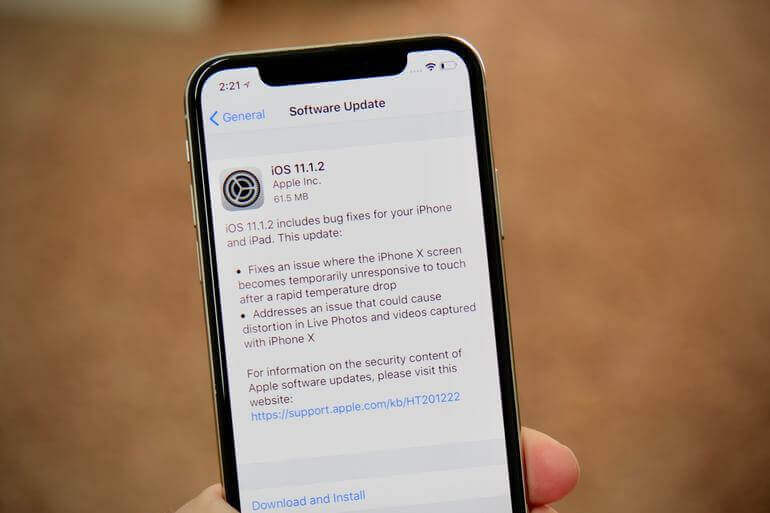
Google’s Project Zero iOS bug hunter Ian Beer has released details about an iOS 11 exploit that could offer up a jailbreak for iOS 11.1.2. Beer last week...
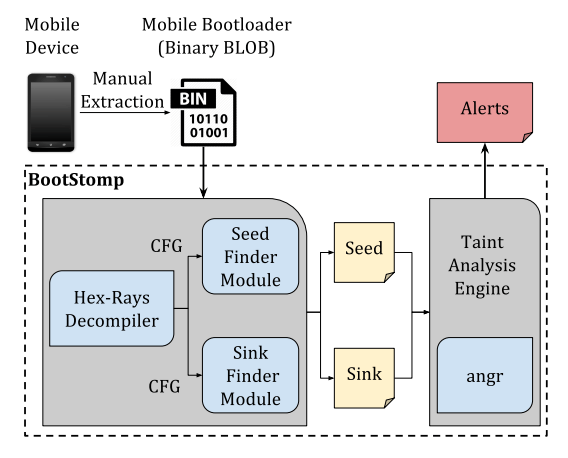
BootStomp is a boot-loader bug finder. It looks for two different class of bugs: memory corruption and state storage vulnerabilities. For more info please...
The keylogging code was embedded in the SynTP.sys file, which is a module of the Synaptics Touchpad driver that ships with HP notebook models. “The logging was...
Some work has been already published regarding the subject of cryptograhic keys security within DRAM. Basically, we need to find something that looks like a...
Kali Linux 2017.3 released, which includes all patches, fixes, updates, and improvements since our last release. In this release, the kernel has been updated...
Prochunter aims to find hidden process with all userspace and most of the kernelspace rootkits. This tool is composed of a kernel module that prints out all...