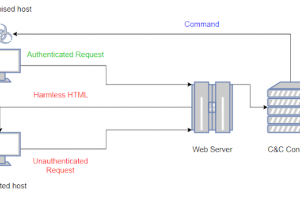
[sc name=”ad_1″] LOLBITS is a C2 framework that uses Microsoft’s Background Intelligent Transfer Service (BITS) to establish the...
Search Results For - JSON
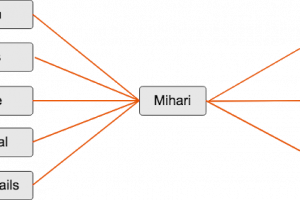
[sc name=”ad_1″] Mihari is a helper to run queries & manage results continuously. Mihari can be used for C2, landing page and phishing hunting...
[sc name=”ad_1″] iblessing iblessing is an iOS security exploiting toolkit, it mainly includes application information collection, static analysis...
[sc name=”ad_1″] A golang utility to spider through a website searching for additional links with support for JavaScript rendering. Install go get ...
[sc name=”ad_1″] A multi-threaded AWS inventory collection tool. The creators of this tool have a recurring need to be able to efficiently collect...
[sc name=”ad_1″] Yeti is a platform meant to organize observables, indicators of compromise, TTPs, and knowledge on threats in a single, unified...
[sc name=”ad_1″] SecGen creates vulnerable virtual machines, lab environments, and hacking challenges, so students can learn security penetration...
[sc name=”ad_1″] Some HTTP parameter names are more commonly associated with one functionality than the others. For example, the parameter ?url=...
[sc name=”ad_1″] A tool for UEFI firmware reverse engineering. UEFI firmware analysis with uefi_retool.py script Usage: Copy...
[sc name=”ad_1″] Defending enterprise networks against attackers continues to present a difficult challenge for blue teams. Prevention has fallen...