Collaborative (mitm) cryptocurrency mining pool in wifi networks. This script performs autonomous MITM attack on WiFi networks. It will inject a javascript in...
Search Results For - Inject Code
Microsoft is addressing unusual of the performance subdividing for fixing patches to relieve the Meltdown and Spectre vulnerabilities. Windows Chief Terry...
Wapiti allows you to audit the security of your websites or web applications. It performs “black-box” scans (it does not study the source code) of...
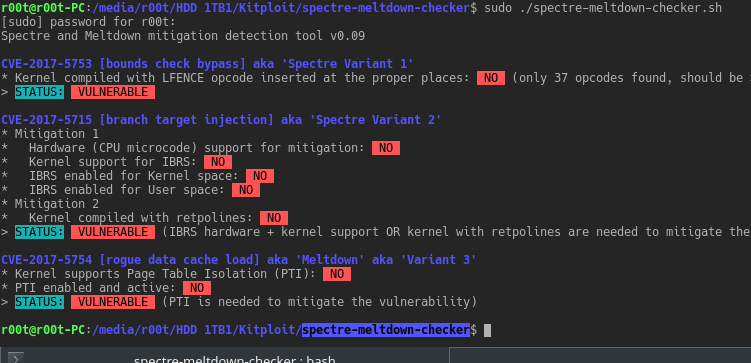
A simple shell script to tell if your Linux installation is vulnerable against the 3 “speculative execution” CVEs: CVE-2017-5753 bounds check...
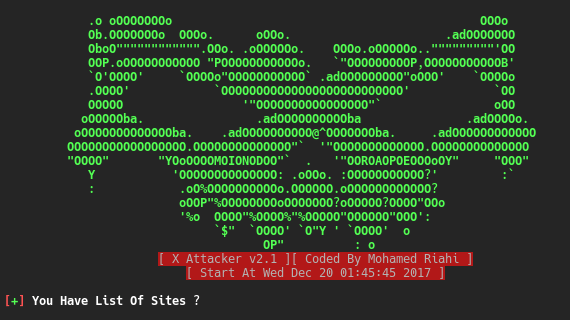
XAttacker is a Website Vulnerability Scanner & Auto Exploiter developed by Mohamed Riahi Auto Cms Detect [1] WordPress : [+] Adblock Blocker [+] WP All...
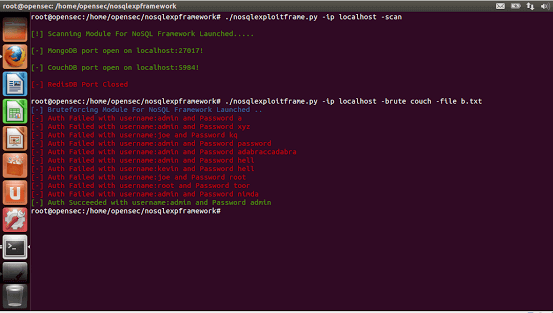
A FrameWork For NoSQL Scanning and Exploitation Framework Authored By Francis Alexander. Added Features: First Ever Tool With Added Support For...
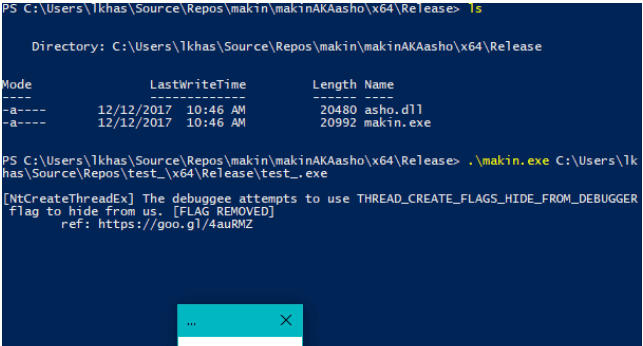
makin is to make initial malware assessment little bit easier, It helps to reveal a debugger detection techniques used by a sample. Supports x64 and x86 How...
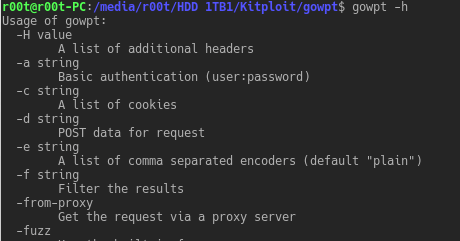
GOWPT is the younger brother of wfuzz a swiss army knife of WAPT, it allow pentester to perform huge activity with no stress at all, just configure it and...
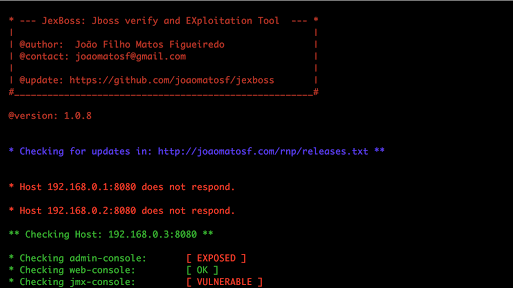
JexBoss is a tool for testing and exploiting vulnerabilities in JBoss Application Server and others Java Platforms, Frameworks, Applications, etc. Requirements...
Wifiphisher is a security tool that mounts automated victim-customized phishing attacks against WiFi clients in order to obtain credentials or infect the...