[sc name=”ad_1″] A team of cybersecurity researchers from the University of New Haven yesterday released a video demonstrating how vulnerabilities...
Search Results For - Infrastructure
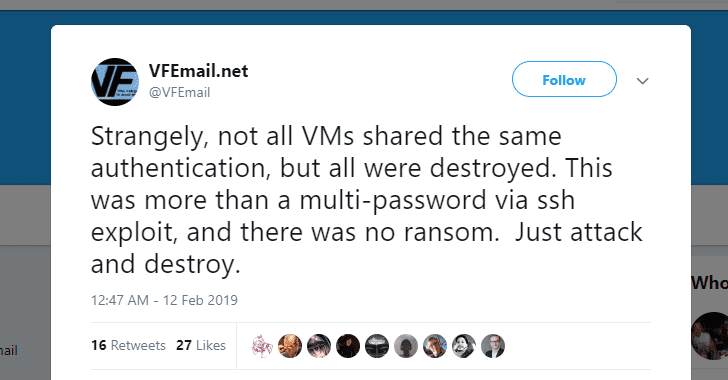
[sc name=”ad_1″] What could be more frightening than a service informing you that all your data is gone—every file and every backup servers are...
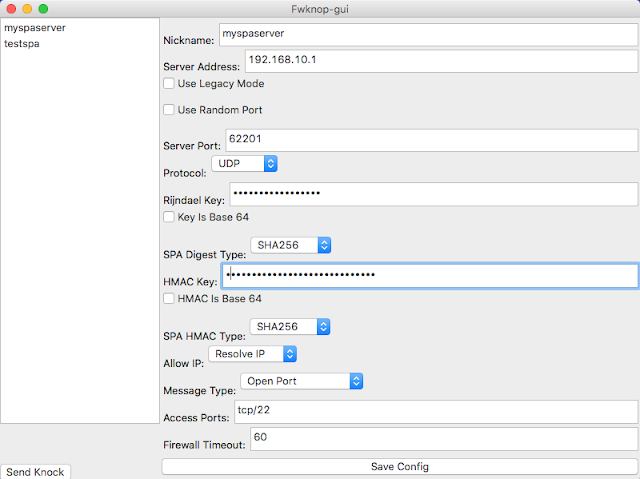
[sc name=”ad_1″] fwknop implements an authorization scheme known as Single Packet Authorization (SPA) for strong service concealment. SPA requires...
[sc name=”ad_1″] The United States Department of Justice (DoJ) announced Wednesday its effort to “map and further disrupt” a botnet...
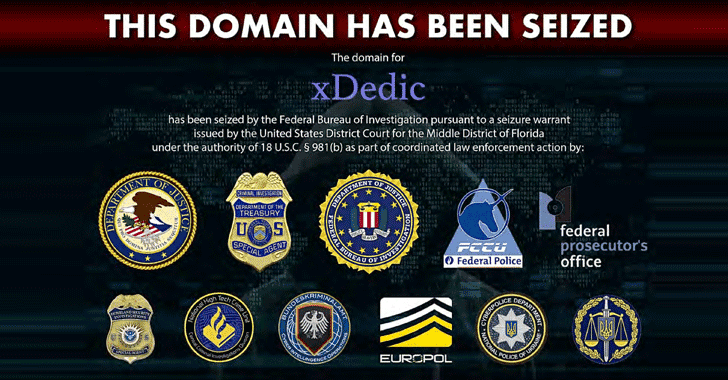
[sc name=”ad_1″] In an international operation involving law enforcement authorities from the U.S. and several European countries, feds have shut...
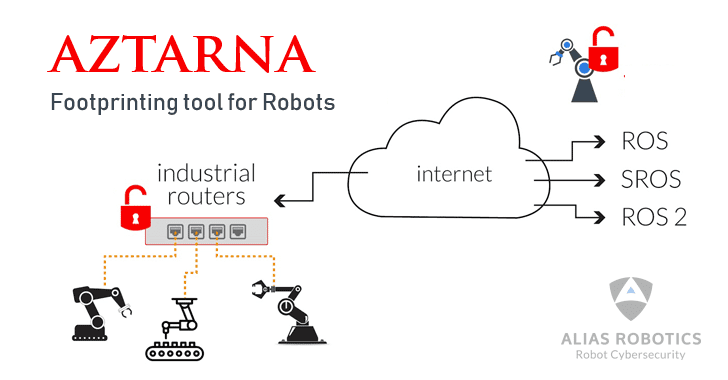
[sc name=”ad_1″] A team at a robot cybersecurity startup has released a free, open-source tool for information security professionals to help them...
[sc name=”ad_1″] The U.S. Department of Homeland Security (DHS) has today issued an “emergency directive” to all federal agencies...
[sc name=”ad_1″] Since most security tools also keep an eye on the network traffic to detect malicious IP addresses, attackers are increasingly...
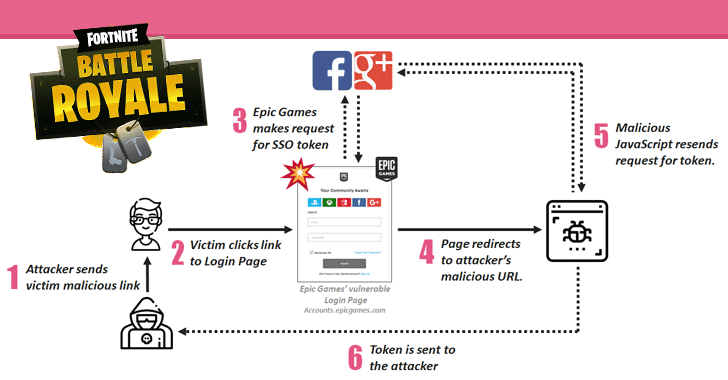
[sc name=”ad_1″] Check Point researchers have discovered multiple security vulnerabilities in Fortnite, a massively popular online battle game, one...
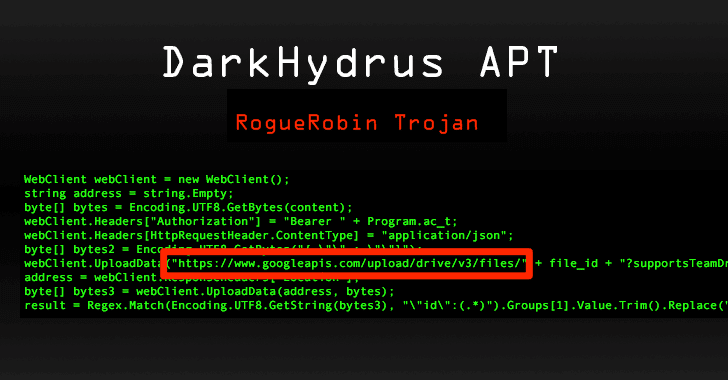
[sc name=”ad_1″] Security researchers have discovered yet another example of how cybercriminals disguise their malware activities as regular...