The Firefox sandboxing innovation confines the browser from the operating system in a way to block web attacks from using a vulnerability in the browser engine...
Search Results For - Information
Similar to questionable stingray devices, DRT’s operations nicknamed “dirt boxes” mimic cellphone pillars, relating to every smartphone within a specific area...
Just over a month after OnePlus was caught collecting personally identifiable information on its users, the Chinese smartphone company has been found leaving a...
Faraday is the Integrated Multiuser Risk Environment you have always been looking for! It maps and leverages all the data you generate in real time, letting...
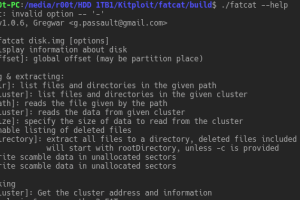
This tool is designed to manipulate FAT filesystems, in order to explore, extract, repair, recover and forensic them. It currently supports FAT12, FAT16 and...
Blockchain.info is a bitcoin cryptocurrency wallet and block explorer service. Started in August 2011, the service presents information on new transactions...
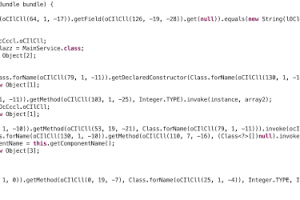
A pattern based Dalvik deobfuscator which uses limited execution to improve semantic analysis. Also, the inspiration for another Android deobfuscator: Simplify...
Google’s research sets out hijacking victims’ email providers and geographic locations. Image: Google Google has released the results of a year...
Today, 9 November 2017, WikiLeaks publishes the source code and development logs to Hive, a major component of the CIA infrastructure to control its malware...
Turns out all they ought to do was ask Apple for help. In a comment the tech titan has issued to the media, it said it “quickly reached out to the FBI after...