A security researcher has discovered several critical vulnerabilities in one of the most popular embedded real-time operating systems—called FreeRTOS—and its...
Search Results For - Information
Slither is a Solidity static analysis framework written in Python 3. It runs a suite of vulnerability detectors, prints visual information about contract...
Facebook has finally been slapped with its first fine of £500,000 for allowing political consultancy firm Cambridge Analytica to improperly gather and...
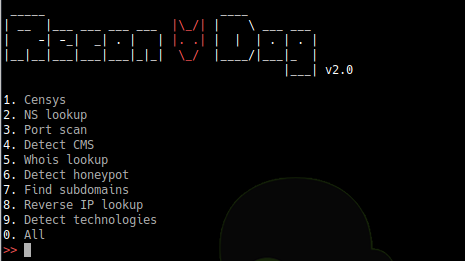
Reconnaissance Swiss Army Knife Main Features Wizard + CLA interface Can extracts targets from STDIN (piped input) and act upon them All the information is...
Nameles provides an easy to deploy, scalable IVT detection and filtering solution that is proven to detect at a high level of accuracy ad fraud and other types...
Discover sub-domains by searching through Certificate Transparency logs. What is CT? Certificate Transparency (CT) is an experimental IETF standard. The goal...
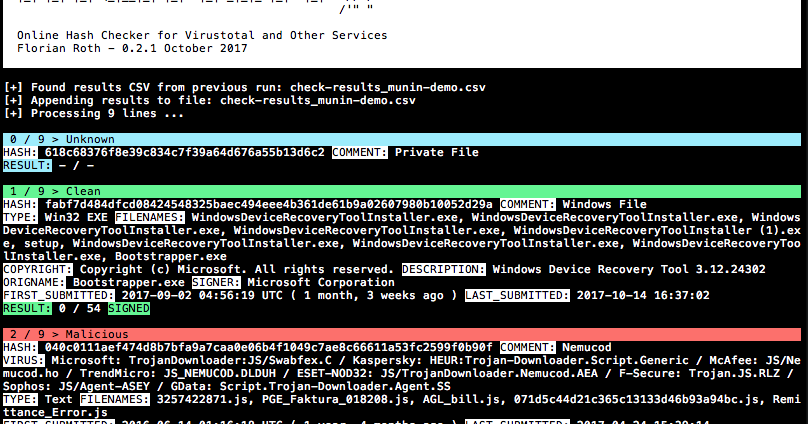
Munin is a online hash checker utility that retrieves valuable information from various online sources The current version of Munin queries the following...
AutoRDPwn is a script created in Powershell and designed to automate the Shadow attack on Microsoft Windows computers. This vulnerability allows a remote...
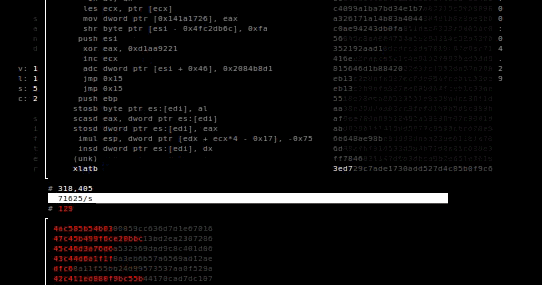
The sandsifter audits x86 processors for hidden instructions and hardware bugs, by systematically generating machine code to search through a processor’s...
ANDRAX The first and unique Penetration Testing platform for Android smartphones What is ANDRAX ANDRAX is a penetration testing platform developed specifically...