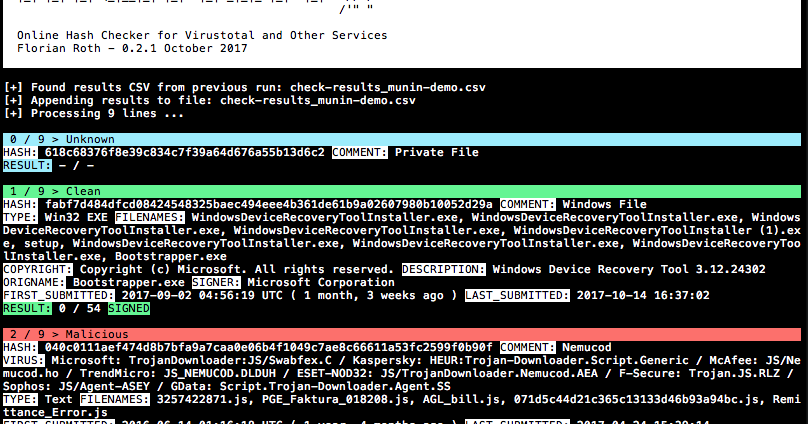
Munin is a online hash checker utility that retrieves valuable information from various online sources
The current version of Munin queries the following services:
- Virustotal
- Malshare
- HybridAnalysis
Note: Munin is based on the script “VT-Checker”, which has been maintained in the LOKI repository.
Usage
usage: munin.py [-h] [-f path] [-c cache-db] [-i ini-file] [-s sample-folder]
[--comment] [-p vt-comment-prefix] [--download]
[-d download_path] [--nocache] [--intense] [--retroverify]
[-r num-results] [--nocsv] [--verifycert] [--sort] [--debug]Online Hash Checker
optional arguments:
-h, --help show this help message and exit
-f path File to process (hash line by line OR csv with hash in
each line - auto-detects position and comment)
-c cache-db Name of the cache database file (default: vt-hash-
db.pkl)
-i ini-file Name of the ini file that holds the API keys
-s sample-folder Folder with samples to process
--comment Posts a comment for the analysed hash which contains
the comment from the log line
-p vt-comment-prefix Virustotal comment prefix
--download Enables Sample Download from Hybrid Analysis. SHA256
of sample needed.
-d download_path Output Path for Sample Download from Hybrid Analysis.
Folder must exist
--nocache Do not use cache database file
--intense Do use PhantomJS to parse the permalink (used to
extract user comments on samples)
--retroverify Check only 40 entries with the same comment and
therest at the end of the run (retrohunt verification)
-r num-results Number of results to take as verification
--nocsv Do not write a CSV with the results
--verifycert Verify SSL/TLS certificates
--sort Sort the input lines (useful for VT retrohunt results)
--debug Debug output
Features
- MODE A: Extracts hashes from any text file based on regular expressions
- MODE B: Walks sample directory and checks hashes online
- Retrieves valuable information from Virustotal via API (JSON response) and other information via permalink (HTML parsing)
- Keeps a history (cache) to query the services only once for a hash that may appear multiple times in the text file
- Cached objects are stored in JSON
- Creates CSV file with the findings for easy post-processing and reporting
- Appends results to a previous CSV if available
Displays
- Hash and comment (comment is the rest of the line of which the hash has been extracted)
- AV vendor matches based on a user defined list
- Filenames used in the wild
- PE information like the description, the original file name and the copyright statement
- Signer of a signed portable executable
- Result based on Virustotal ratio
- First and last submission
- Tags for certain indicators: Harmless, Signed, Expired, Revoked, MSSoftware
Extra Checks
- Queries Malshare.com for sample uploads
- Queries Hybrid-Analysis.com for present analysis
- Imphash duplicates in current batch > allows you to spot overlaps in import table hashes
Getting started
- Download / clone the repo
- Install required packages:
pip3 install -r requirements.txt(on macOS add--user) - (optional: required for –intense mode) Download PhantomJS and place it in your $PATH, e.g. /usr/local/bin http://phantomjs.org/download.html
- Set the API key for the different services in the
munin.inifile - Use the demo file for a first run:
python munin.py -f munin-demo.txt --nocache
Typical Command Lines
Process a Virustotal Retrohunt result and sort the lines before checking so that matched signatures are checked in blocks
python munin.py -f my.ini -f ~/Downloads/retro_huntProcess an IOC file and show who commented on these samples on Virustotal (uses PhantomJS, higher CPU usage)
python munin.py -f my.ini -f ~/Downloads/misp-event-1234.csv --sort --intenseProcess a directory with samples and check their hashes online
python munin.py -f my.ini -s ~/malware/case34Get the API Keys used by Munin
Virustotal
- Create an account here https://www.virustotal.com/#/join-us
- Check
Profile > My API keyfor your public API key
Malshare
Register here https://malshare.com/register.php
Hybrid Analysis
- Create an account here https://www.hybrid-analysis.com/signup
- After login, check
Profile > API key


















Add Comment