MAC Changer is an utility that makes the maniputation of MAC addresses of network interfaces easier. A media access control (Mac) address of a device is a...
Search Results For - Identifier
This type of abusive conduct is possible because of a configuration flaw in the login handlers included with all browsers, login managers that allow browsers...
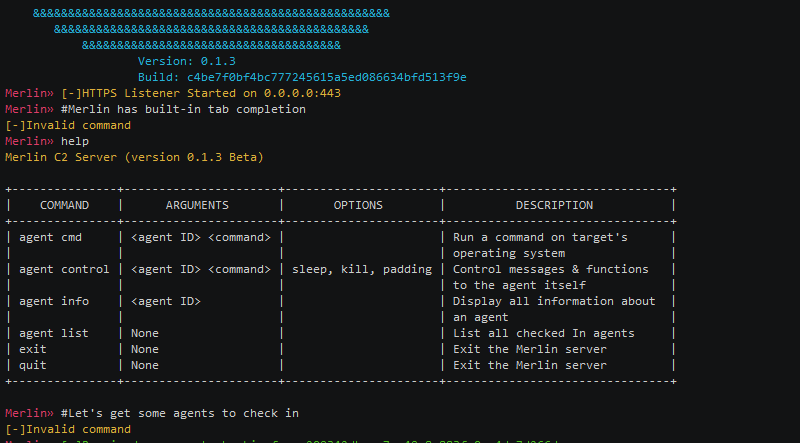
Merlin is a cross-platform post-exploitation framework that leverages HTTP/2 communications to evade inspection. HTTP/2 is a relatively new protocol that...
Google’s research sets out hijacking victims’ email providers and geographic locations. Image: Google Google has released the results of a year...
Device drivers are an essential part in modern Unix-like systems to handle operations on physical devices, from hard disks and printers to digital cameras and...
Network Security Monitoring (NSM) is, put simply, monitoring your network for security related events. It might be proactive, when used to identify...
Unfortunately, it looks like the method is still in effect. Philip Neustrom, the co-founder of Shotwell Labs, lately found two demo websites that would pass...