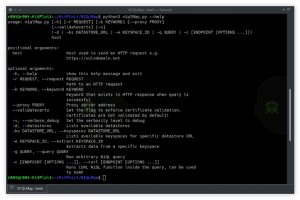
[sc name=”ad_1″] N1QLMap is an N1QL exploitation tool. Currently works with Couchbase database. The tool supports data extraction and performing...
Search Results For - IDA Pro
[sc name=”ad_1″] nginx Docker image secure by default. Avoid the hassle of following security best practices each time you need a web server or...
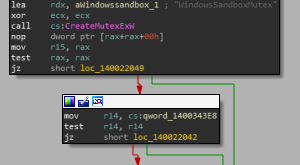
[sc name=”ad_1″] wsb-detect enables you to detect if you are running in Windows Sandbox (“WSB”). The sandbox is used by Windows...
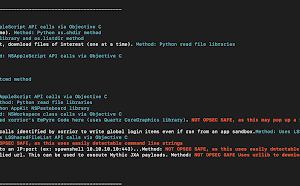
[sc name=”ad_1″] MacC2 is a macOS post exploitation tool written in python that uses Objective C calls or python libraries as opposed to command...
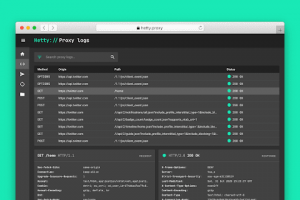
[sc name=”ad_1″] Hetty is an HTTP toolkit for security research. It aims to become an open source alternative to commercial software like Burp...
[sc name=”ad_1″] What the heck is a ferox anyway? Ferox is short for Ferric Oxide. Ferric Oxide, simply put, is rust. The name rustbuster was...
[sc name=”ad_1″] A curated list of Android Security materials and resources For Pentesters and Bug Hunters. Blog AAPG – Android application...
[sc name=”ad_1″] A vulnerability scanner for container images and filesystems. Easily install the binary to try it out. Features Scan the contents...
[sc name=”ad_1″] Enumerate valid usernames from Office 365 using ActiveSync, Autodiscover, or office.com login page. Usage o365enum will read...
[sc name=”ad_1″] h2cSmuggler smuggles HTTP traffic past insecure edge-server proxy_pass configurations by establishing HTTP/2 cleartext (h2c)...