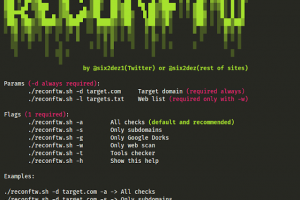
[sc name=”ad_1″] This is a simple script intended to perform a full recon on an objective with multiple subdomains tl;dr Requires Go Run ./install...
Search Results For - IDA Pro
[sc name=”ad_1″] A collection of cool tools used by Mobile hackers. Happy hacking , Happy bug-hunting Weapons OS Type Name Description All Analysis...
[sc name=”ad_1″] HosTaGe is a lightweight, low-interaction, portable, and generic honeypot for mobile devices that aims on the detection of...
[sc name=”ad_1″] BigBountyRecon tool utilises 58 different techniques using various Google dorks and open source tools to expedite the process of...
[sc name=”ad_1″] SARENKA is an Open Source Intelligence (OSINT) tool which helps you obtaining and understanding Attack Surface. The main goal is...
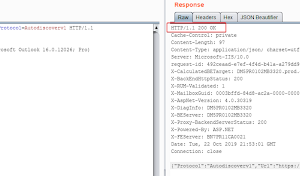
[sc name=”ad_1″] A script that can see if an email address is valid in Office365. This does not perform any login attempts, is unthrottled, and is...
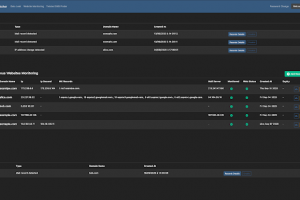
[sc name=”ad_1″] Watcher is a Django & React JS automated platform for discovering new potentially cybersecurity threats targeting your...
[sc name=”ad_1″] E9Patch is a powerful static binary rewriting tool for x86_64 Linux ELF binaries. E9Patch is: Scalable: E9Patch can reliably...
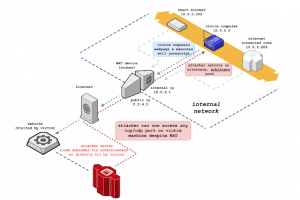
[sc name=”ad_1″] NAT Slipstreaming allows an attacker to remotely access any TCP/UDP services bound to a victim machine, bypassing the...
[sc name=”ad_1″] Damn Vulnerable Bank Android Application aims to provide an interface for everyone to get a detailed understanding with internals...