Facebook has finally been slapped with its first fine of £500,000 for allowing political consultancy firm Cambridge Analytica to improperly gather and...
Search Results For - Highlight
A framework based on the Fiddler web debugger to study Exploit Kits, malvertising and malicious traffic in general. Installation Download and install the...
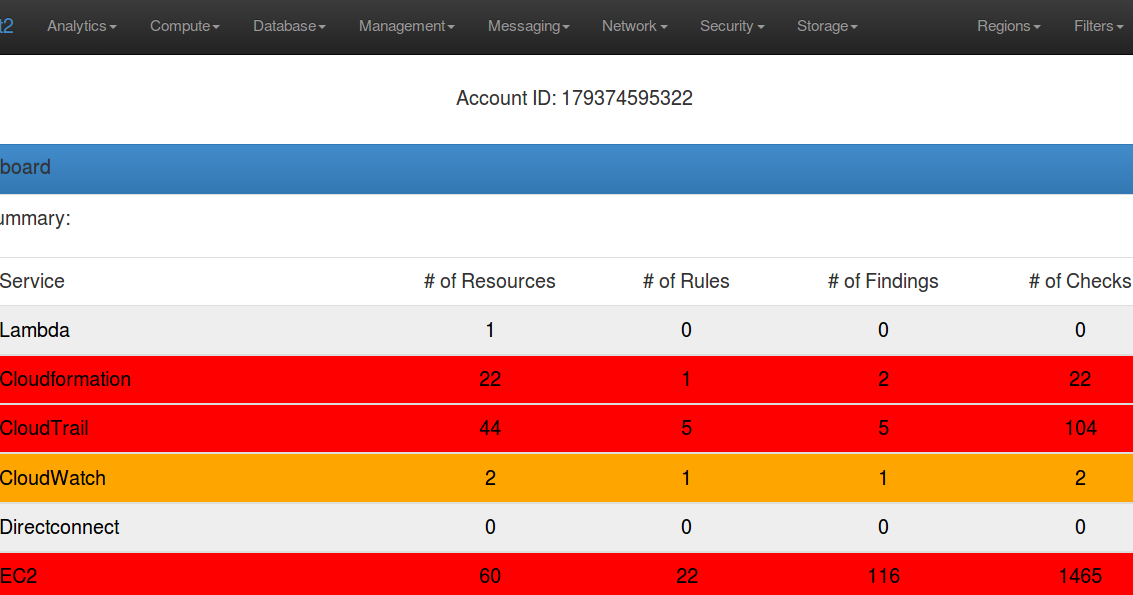
Scout2 is a security tool that lets AWS administrators assess their environment’s security posture. Using the AWS API, Scout2 gathers configuration data...
Seeker utilizes HTML5, Javascript, JQuery and PHP to grab Device Information and GeoLocation with High Accuracy. Seeker Hosts a fake website on Apache Server...
Evil Remote Administration Tool (RAT) for macOS/OS X Features Emulate a terminal instance Simple extendable module system No bot dependencies (pure python)...
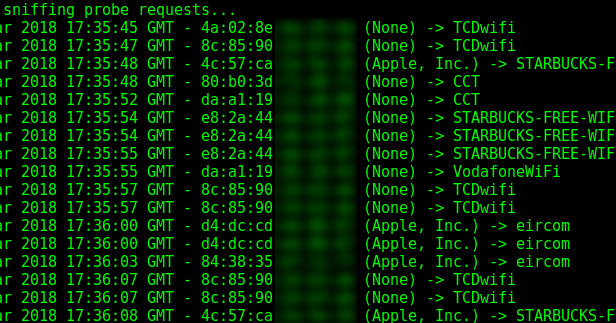
Toolkit allowing to sniff and display the Wi-Fi probe requests passing near your wireless interface. Probe requests are sent by a station to elicit information...
Many investors that want to enter the cryptocurrency market have never traded any form of a financial instrument before. Most of them, however, have some form...
Author: Marshall Taylor Blockchains and their cryptocurrencies are energetically following a path similar to other major leaps in technology that have come...
pwnedOrNot is a python script which checks if the email account has been compromised in a data breach, if the email account is compromised it proceeds to find...
A tool for reverse engineering 3rd party, closed, binary Android apps. It can decode resources to nearly original form and rebuild them after making some...