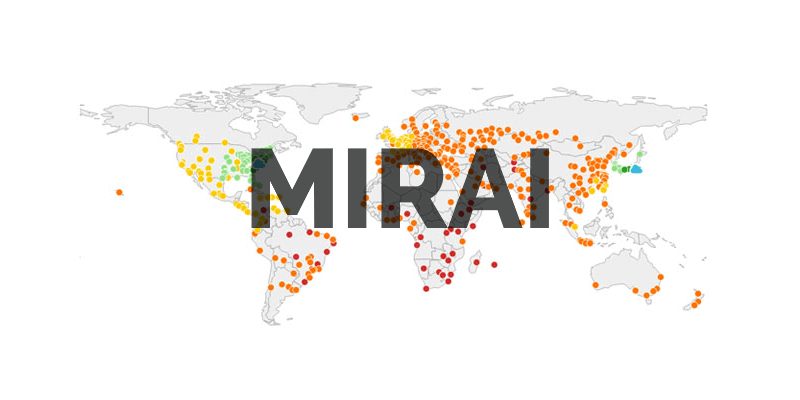
The U.S. federal officials have arrested two hackers who have pleaded guilty to computer-crimes charges for creating and distributing Mirai botnet that...
Search Results For - Hackers
Apple is one of the biggest companies today, but its devices are not free from issues. Recently, it was reported that the company’s HomeKit software used to...
Newly uncovered vulnerabilities in a popular brand of indoor internet-connected cameras could be exploited by attackers in order to gain complete control of...
Google’s research sets out hijacking victims’ email providers and geographic locations. Image: Google Google has released the results of a year...
This scam email is nearly well designed. The scammers are using a template system to create individualized reports with specific recipient data. This works...
Cybercriminals decided to use the Search Engine Optimization (SEO) to make their malicious links more widespread in the search results, allowing them to gain...
In 2013, Hackers apparently gained access to the Trump Organization’s domain booking account and created at least 250 website subdomains that cybersecurity...
Oracle Identity Manager (OIM) allows companies to manage the entire user life-cycle overall company resources both within and behind a firewall. Within Oracle...
Performs OSINT scan on email/domain/ip_address/organization using OSINT-SPY. It can be used by Data Miners, Infosec Researchers, Penetration Testers and cyber...
[sc name=”ad_1″] Although 2020 has been the worst year since 1945, as last year, this year we made a ranking with the most popular tools between...