[sc name=”ad_1″] Why would someone bother to hack a so-called “ultra-secure encrypted database that is being protected behind 13 feet high...
Search Results For - Exposing
[sc name=”ad_1″] The U.S. Department of Homeland Security (DHS) has today issued an “emergency directive” to all federal agencies...
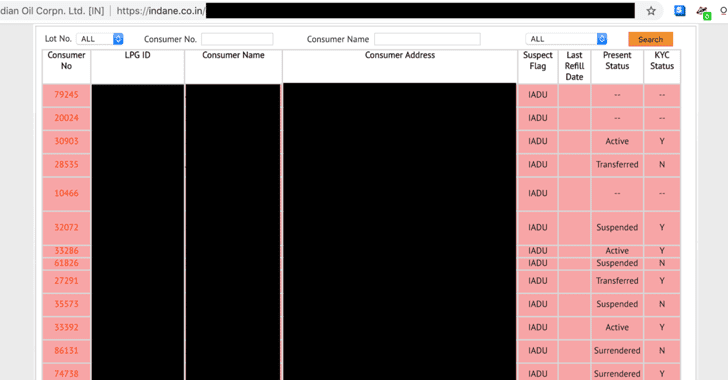
[sc name=”ad_1″] A massive government data belonging to the Oklahoma Department of Securities (ODS) was left unsecured on a storage server for at...
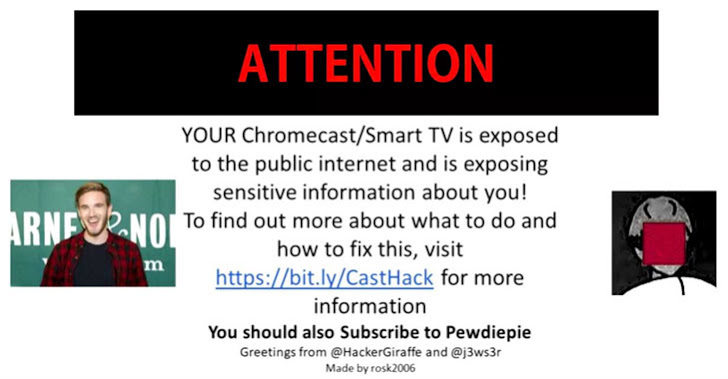
[sc name=”ad_1″] A group of hackers has hijacked tens of thousands of Google’s Chromecast streaming dongles, Google Home smart speakers and...
[sc name=”ad_1″] British and Dutch data protection regulators Tuesday hit the ride-sharing company Uber with a total fine of $1,170,892 (~ 1.1...
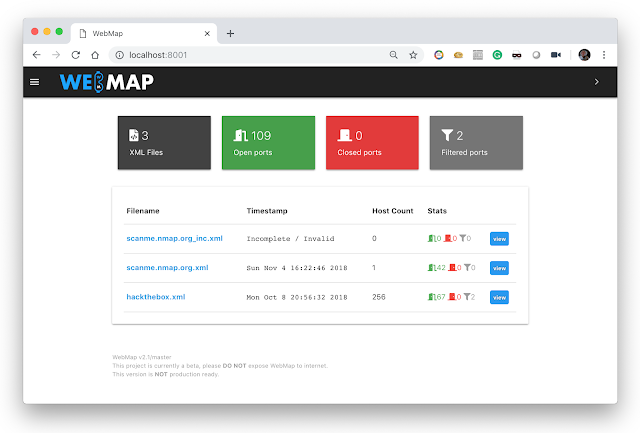
A Web Dashbord for Nmap XML Report Usage You should use this with docker, just by sending this command: $ mkdir /tmp/webmap $ docker run -d --name webmap -h...
A security researcher has discovered several critical vulnerabilities in one of the most popular embedded real-time operating systems—called FreeRTOS—and its...
As per many security reports, managements systems of buildings all over the world have improved dramatically, however, their security is still at a large risk...
Even software that has been built with secure development procedures may still be vulnerable to attack, due to flaws in the interpreted programming languages...
Google’s research sets out hijacking victims’ email providers and geographic locations. Image: Google Google has released the results of a year...