[sc name=”ad_1″] A collection of cool tools used by Web hackers. Happy hacking , Happy bug-hunting. Weapons Type Name Description Popularity...
Search Results For - Exploits
[sc name=”ad_1″] A list of useful payloads and bypasses for Web Application Security. Feel free to improve with your payloads and techniques ...
[sc name=”ad_1″] Modern Denial-of-service ToolKit Main window Methods: Method Target Description SMS +PHONE SMS & CALL FLOOD NTP IP:PORT NTP...
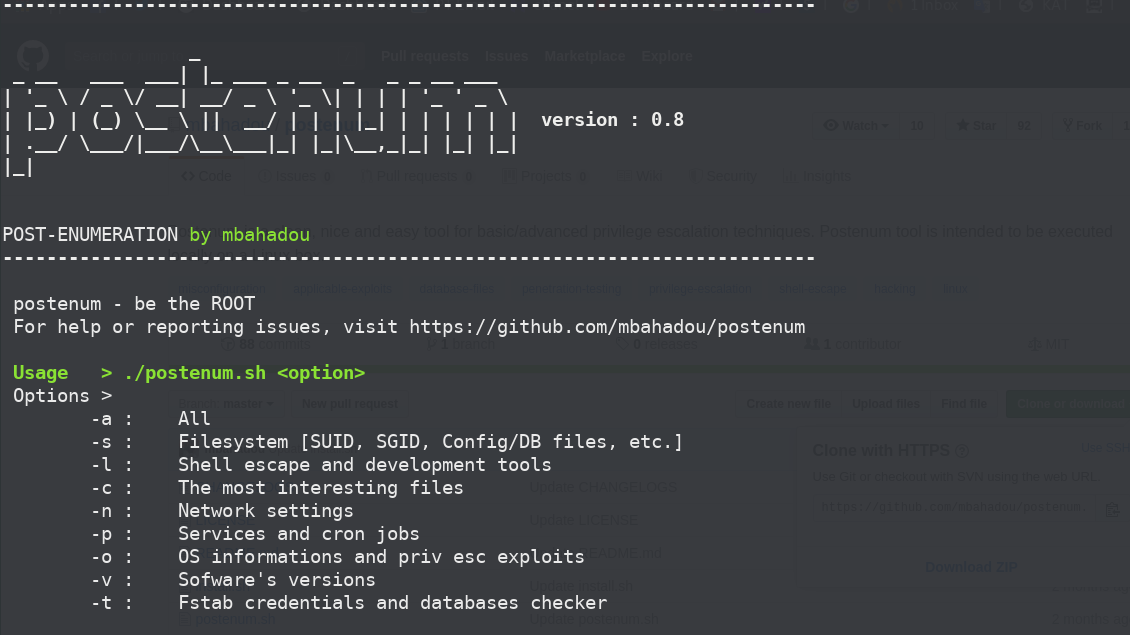
[sc name=”ad_1″] Postenum is a clean, nice and easy tool for basic/advanced privilege escalation vectors/techniques. Postenum tool is intended to...
[sc name=”ad_1″] Lockdoor Framework : A Penetration Testing Framework With Cyber Security Resources. 09/2019 : 1.0Beta Information Gathring Tools...
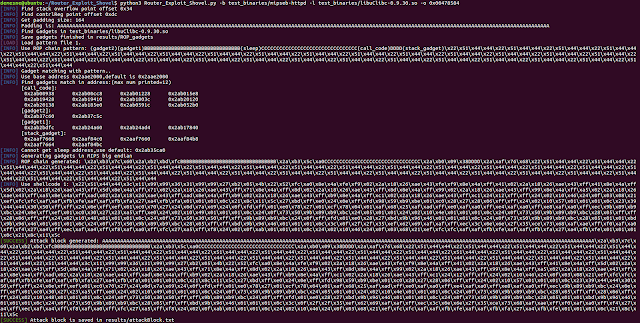
[sc name=”ad_1″] Automated Application Generation for Stack Overflow Types on Wireless Routers. Router exploits shovel is an automated application...
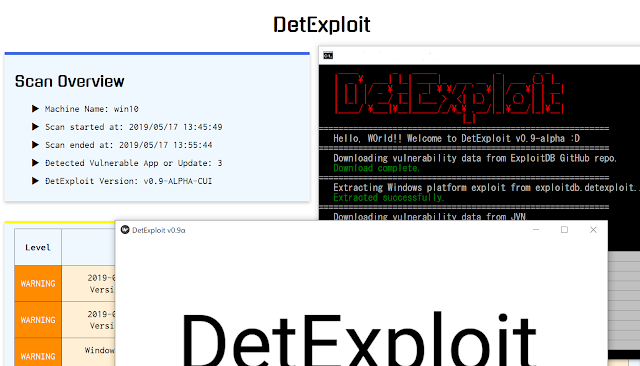
[sc name=”ad_1″] DetExploit is software that detect vulnerable applications and not-installed important OS updates on the system, and notify them...
[sc name=”ad_1″] Libssh2, a popular open source client-side C library implementing the SSHv2 protocol, has released the latest version of its...
[sc name=”ad_1″] Various cyber criminal groups and individual hackers are still exploiting a recently patched critical code execution vulnerability...
[sc name=”ad_1″] Adobe users would feel lighter this month, as Adobe has released patches for just two security vulnerability in its March Security...