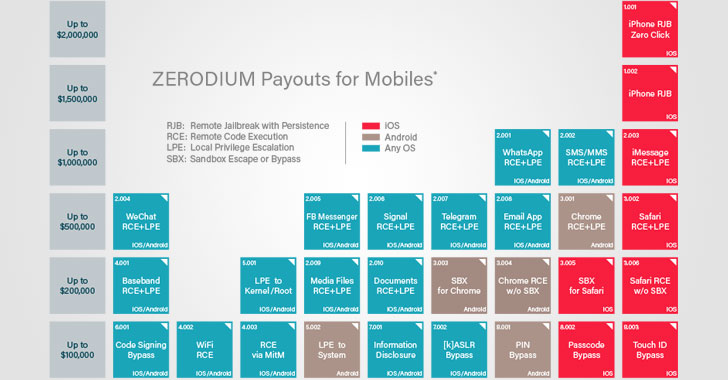
[sc name=”ad_1″] About Ghost Framework Ghost Framework is an Android post-exploitation framework that exploits the Android Debug Bridge to remotely...
Search Results For - Exploits
[sc name=”ad_1″] Security researchers have uncovered a new variant of the infamous Mirai Internet of Things botnet, this time targeting embedded...
[sc name=”ad_1″] Well, there’s some good news for hackers and vulnerability hunters, though terrible news for tech manufacturers! Exploit...
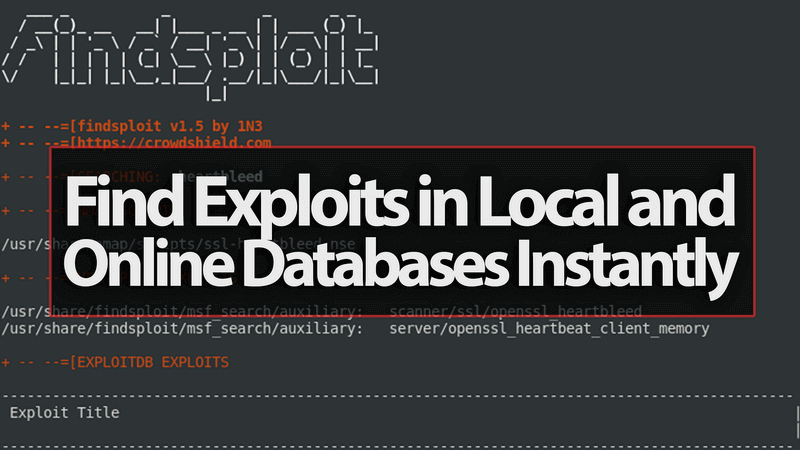
Findsploit is a simple bash script to quickly and easily search both local and online exploit databases. Findsploit: Installation: git clone cd Findsploit...
[sc name=”ad_1″] CDK is an open-sourced container penetration toolkit, designed for offering stable exploitation in different slimmed containers...
[sc name=”ad_1″] BigBountyRecon tool utilises 58 different techniques using various Google dorks and open source tools to expedite the process of...
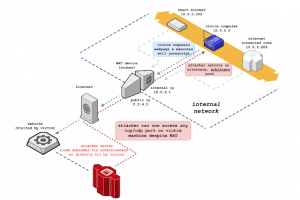
[sc name=”ad_1″] NAT Slipstreaming allows an attacker to remotely access any TCP/UDP services bound to a victim machine, bypassing the...
[sc name=”ad_1″] Stegseek is a lightning fast steghide cracker that can be used to extract hidden data from files. It is built as a fork of the...
[sc name=”ad_1″] Features: Hacker Dashboard Hacker News [thehackernews.com/] New Exploits [Exploit-db.com] Hacking Tutorials Video [youtube.com]...
[sc name=”ad_1″] Based on pywebfuzz, Py3webfuzz is a Python3 module to assist in the identification of vulnerabilities in web applications, Web...