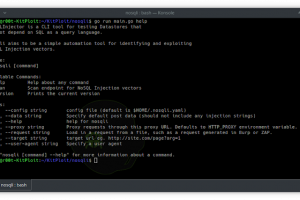
[sc name=”ad_1″] NoSQL scanner and injector. About Nosqli I wanted a better nosql injection tool that was simple to use, fully command line based...
Search Results For - Exploiting
[sc name=”ad_1″] h2cSmuggler smuggles HTTP traffic past insecure edge-server proxy_pass configurations by establishing HTTP/2 cleartext (h2c)...
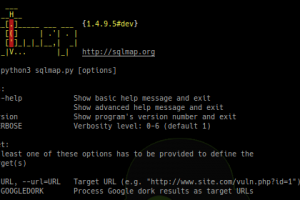
[sc name=”ad_1″] SQLMap is an open source penetration testing tool that automates the process of detecting and exploiting SQL injection flaws and...
[sc name=”ad_1″] A python based tool for exploiting and managing Android devices via ADB Currently on development Screenrecord Stream Screenrecord...
[sc name=”ad_1″] Git All the Payloads! A collection of web attack payloads. Pull requests are welcome! Usage run ./get.sh to download external...
[sc name=”ad_1″] Undetectable Reverse shell & Xor encrypting with custom KEY(FUD Metasploit Rat) bypass Top Antivirus like...
[sc name=”ad_1″] A collection of cool tools used by Web hackers. Happy hacking , Happy bug-hunting. Weapons Type Name Description Popularity...
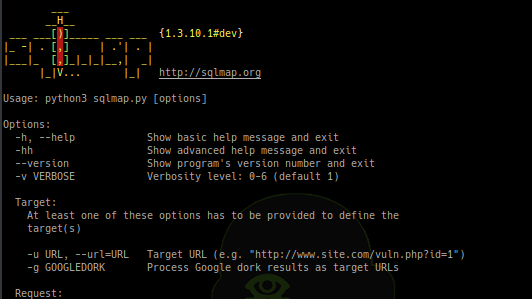
[sc name=”ad_1″] SQLMap is an open source penetration testing tool that automates the process of detecting and exploiting SQL injection flaws and...
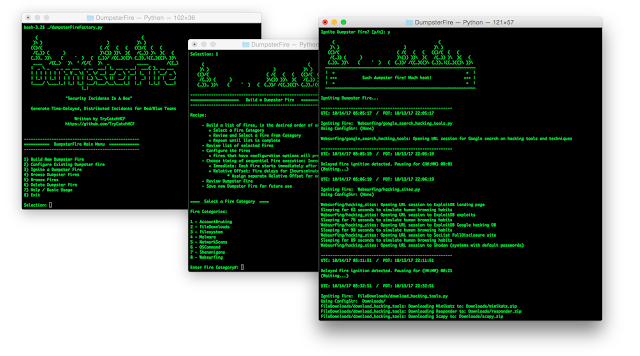
[sc name=”ad_1″] DumpsterFire Toolset – “Security Incidents In A Box!” The DumpsterFire Toolset is a modular, menu-driven, cross...
[sc name=”ad_1″] A File Inclusion & Directory Traversal fuzzing, enumeration & exploitation tool. FDsploit menu: $ python fdsploit.py -h...