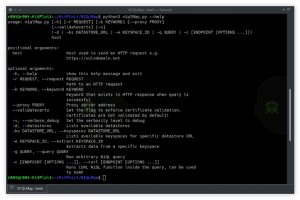
[sc name=”ad_1″] N1QLMap is an N1QL exploitation tool. Currently works with Couchbase database. The tool supports data extraction and performing...
Search Results For - Exploiting
[sc name=”ad_1″] iblessing iblessing is an iOS security exploiting toolkit, it mainly includes application information collection, static analysis...
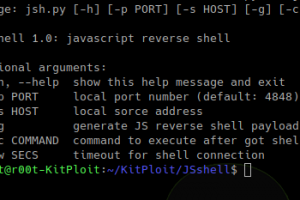
[sc name=”ad_1″] JSshell – a JavaScript reverse shell. This using for exploit XSS remotely, help to find blind XSS, … This tool works...
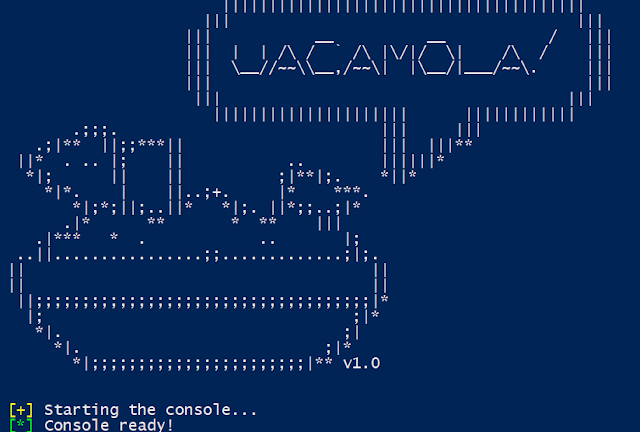
[sc name=”ad_1″] UAC-A-Mola is a tool that allows security researchers to investigate new UAC bypasses, in addition to detecting and exploiting...
[sc name=”ad_1″] Cybercriminals have actively started exploiting an already patched security vulnerability in the wild to install cryptocurrency...
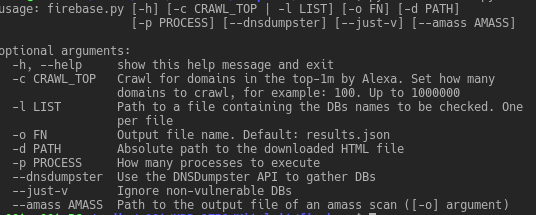
Exploiting vulnerable/misconfigured Firebase databases Prerequisites Non-standard python modules: dnsdumpster bs4 requests Installation If the following...
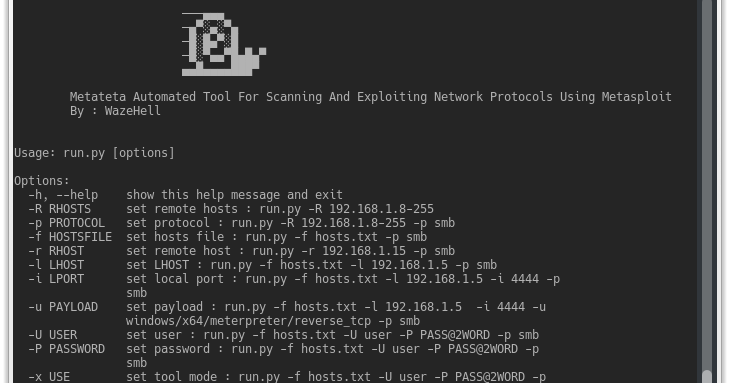
Metateta Automated Tool For Scanning And Exploiting Network Protocols Using Metasploit For faster pen testing for large networks What You Can Do Scanning with...
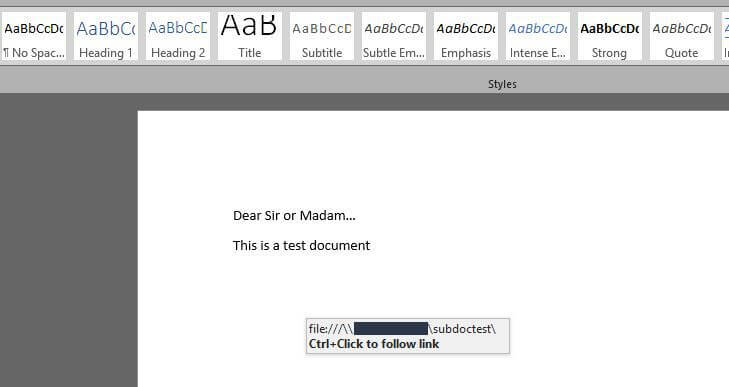
Security researchers from Rhino Labs (a US-based cyber-security firm) have found that cyber criminals can use a Microsoft Word feature dubbed subDoc to fool...
[sc name=”ad_1″] BigBountyRecon tool utilises 58 different techniques using various Google dorks and open source tools to expedite the process of...
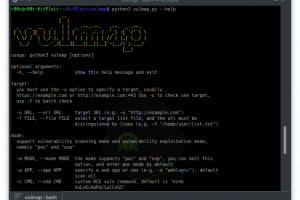
[sc name=”ad_1″] Vulmap is a vulnerability scanning tool that can scan for vulnerabilities in Web containers, Web servers, Web middleware, and CMS...