It had earlier banned an internet-associated doll called, My Friend Cayla, for similar reasons. Telecoms regulator the Federal Network Agency urged parents who...
Search Results For - Encryption
SpookFlare has a different perspective to bypass security measures and it gives you the opportunity to bypass the endpoint countermeasures at the client-side...
Forever 21 is investigating a potential data breach which may have compromised customer information and payment cards. On Tuesday, the US clothing retailer...
The federal government on Tuesday issued an alert detailing the North Korean government’s use of malware known as FALLCHILL, warning that North Korea has...
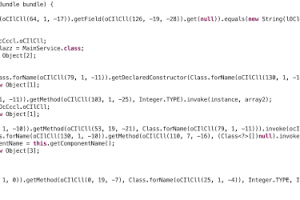
A pattern based Dalvik deobfuscator which uses limited execution to improve semantic analysis. Also, the inspiration for another Android deobfuscator: Simplify...
Security GNU/Linux distribution designed with cloud pentesting and IoT security in mind. It includes a full portable laboratory for security and digital...
DNS over TLS is a protocol where DNS inquiries will be encrypted to the equivalent level as HTTPS and therefore a DNS can’t actually log or see the websites...
A wrapper tool for shadowsocks to consistently bypass firewalls. Quick start Automatically connect The easiest way to run this tool is just type ssct in...
Security researchers have discovered several key management vulnerabilities in the core of Wi-Fi Protected Access II (WPA2) protocol that could allow an...
DET (is provided AS IS), is a proof of concept to perform Data Exfiltration using either single or multiple channel(s) at the same time. This is a Proof of...