[sc name=”ad_1″] An organizational asset and vulnerability management tool, with Jira integration, designed for generating application security...
Search Results For - Email
[sc name=”ad_1″] Linux evil toolkit is a framework that aims to centralize, standardize and simplify the use of various security tools for pentest...
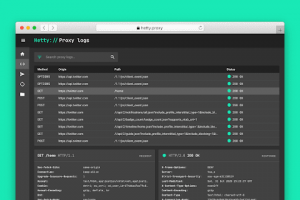
[sc name=”ad_1″] Hetty is an HTTP toolkit for security research. It aims to become an open source alternative to commercial software like Burp...
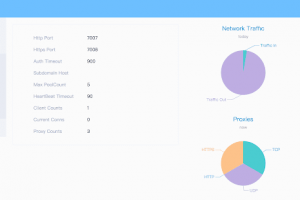
[sc name=”ad_1″] The Nethive Project provides a Security Information and Event Management (SIEM) insfrastructure empowered by CVSS automatic...
[sc name=”ad_1″] Manuka is an Open-source intelligence (OSINT) honeypot that monitors reconnaissance attempts by threat actors and generates...
[sc name=”ad_1″] Takeover AWS ips and have a working POC for Subdomain Takeover. Idea is simple Get subdomains. Do reverse lookups to only save AWS...
[sc name=”ad_1″] Enumerate valid usernames from Office 365 using ActiveSync, Autodiscover, or office.com login page. Usage o365enum will read...
[sc name=”ad_1″] This Is Advance Phishing Tool! OTP PHISHING SPECIAL OTP BYPASS VIDEO WORKED Social Media Hack Link Installation Termux Whatsapp...
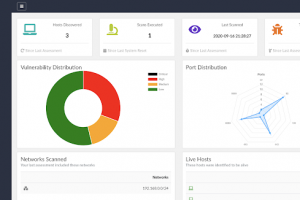
[sc name=”ad_1″] NERVE is a vulnerability scanner tailored to find low-hanging fruit level vulnerabilities, in specific application configurations...
[sc name=”ad_1″] A Fast Reverse Proxy To Help You Expose A Local Server Behind A NAT Or Firewall To The Internet. Development Status frp is under...