A former operations manager existed for Facebook’s privacy works said the company “prioritized data gathering from its users overprotecting them from abuse.”...
Search Results For - EXIST
Newly uncovered vulnerabilities in a popular brand of indoor internet-connected cameras could be exploited by attackers in order to gain complete control of...
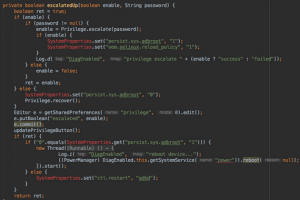
Nishang is an open source framework and collection of powerful PowerShell scripts and payloads that you can use during penetration testing audit, post...
Just over a month after OnePlus was caught collecting personally identifiable information on its users, the Chinese smartphone company has been found leaving a...
Bitcoin surged on Monday, recovering more than $1,000 after losing almost a third of its value in less than four days as traders bought back into the volatile...
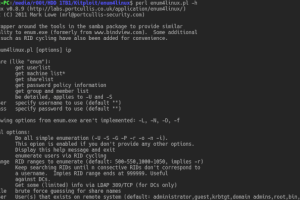
A Linux alternative to enum.exe for enumerating data from Windows and Samba hosts. Enum4linux is a tool for enumerating information from Windows and Samba...
Today, 9 November 2017, WikiLeaks publishes the source code and development logs to Hive, a major component of the CIA infrastructure to control its malware...
CrunchRAT currently supports the following features: File upload File download Command execution It is currently single-threaded (only one task at a time), but...
A Facebook post promoting rape videos was also allowed to stay online despite being informed several times, the court listened, while police in the western...
Cybercriminals decided to use the Search Engine Optimization (SEO) to make their malicious links more widespread in the search results, allowing them to gain...