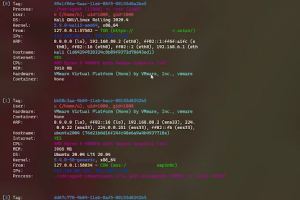
[sc name=”ad_1″] CDK is an open-sourced container penetration toolkit, designed for offering stable exploitation in different slimmed containers...
Search Results For - Discover
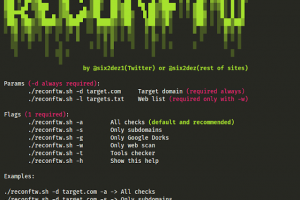
[sc name=”ad_1″] This is a simple script intended to perform a full recon on an objective with multiple subdomains tl;dr Requires Go Run ./install...
[sc name=”ad_1″] A collection of cool tools used by Mobile hackers. Happy hacking , Happy bug-hunting Weapons OS Type Name Description All Analysis...
[sc name=”ad_1″] BigBountyRecon tool utilises 58 different techniques using various Google dorks and open source tools to expedite the process of...
[sc name=”ad_1″] Collect OSINT for GitLab groups and members and search the group and group members’ snippets, issues, and issue discussions...
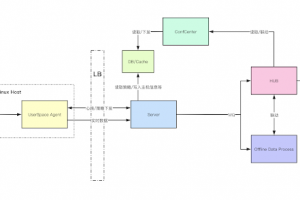
[sc name=”ad_1″] ByteDance-HIDS is a Cloud-Native Host-Based Intrusion Detection solution project to provide next-generation Threat Detection and...
[sc name=”ad_1″] linux post-exploitation framework made by linux user Still under active development 中文介绍 check my blog for updates how to use what...
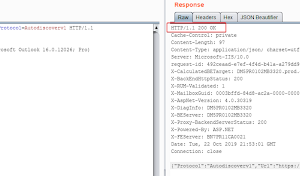
[sc name=”ad_1″] A script that can see if an email address is valid in Office365. This does not perform any login attempts, is unthrottled, and is...
[sc name=”ad_1″] Cross-Site Scripting (XSS) is one of the most well known web application vulnerabilities. It even has a dedicated chapter in the...
[sc name=”ad_1″] HyperDbg is designed with a focus on using modern hardware technologies to provide new features to the reverse engineering world...