SpookFlare has a different perspective to bypass security measures and it gives you the opportunity to bypass the endpoint countermeasures at the client-side...
Search Results For - Detection
Security researchers have discovered a new, sophisticated form of malware based on the notorious Zeus banking Trojan that steals more than just bank account...
The GOSINT framework is a project used for collecting, processing, and exporting high quality indicators of compromise (IOCs). GOSINT allows a security analyst...
This tool is related to ACM CCS 2017 conference paper #124 Return of the Coppersmith’s Attack: Practical Factorization of Widely Used RSA Moduli. It enables...
TrevorC2 is a client/server model for masking command and control through a normally browsable website. Detection becomes much harder as time intervals are...
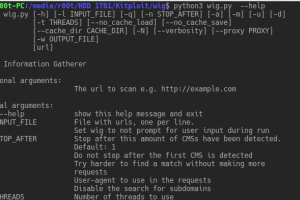
wig is a web application information gathering tool, which can identify numerous Content Management Systems and other administrative applications. The...
Network Security Monitoring (NSM) is, put simply, monitoring your network for security related events. It might be proactive, when used to identify...
We are excited to announce this major release of auditing tool Lynis. Several big changes have been made to core functions of Lynis. These changes are the next...
Are you a proud iPhone owner? If yes, this could freak you up. Trust me! Your iPhone has a serious privacy concern that allows iOS app developers to take your...
Qubes OS is a security-oriented operating system (OS). The OS is the software that runs all the other programs on a computer. Some examples of popular OSes are...