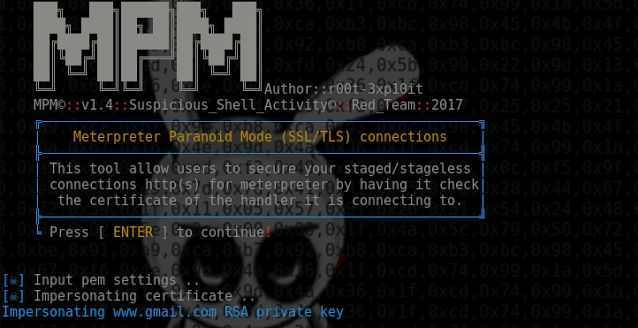
Meterpreter_Paranoid_Mode.sh allows users to secure your staged/stageless connection for Meterpreter by having it check the certificate of the handler it is...
Search Results For - Detection
Sigma is a generic and open signature format that allows you to describe relevant log events in a straight forward manner. The rule format is very flexible...
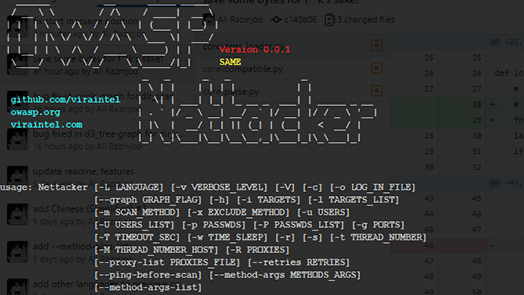
OWASP Nettacker project is created to automate information gathering, vulnerability scanning and eventually generating a report for networks, including...
NXcrypt is a polymorphic ‘python backdoors’ crypter written in python by Hadi Mene (h4d3s) . The output is fully undetectable. NXcrypt can inject...
DNSExfiltrator allows for transfering (exfiltrate) a file over a DNS request covert channel. This is basically a data leak testing tool allowing to exfiltrate...
Wapiti allows you to audit the security of your websites or web applications. It performs “black-box” scans (it does not study the source code) of...
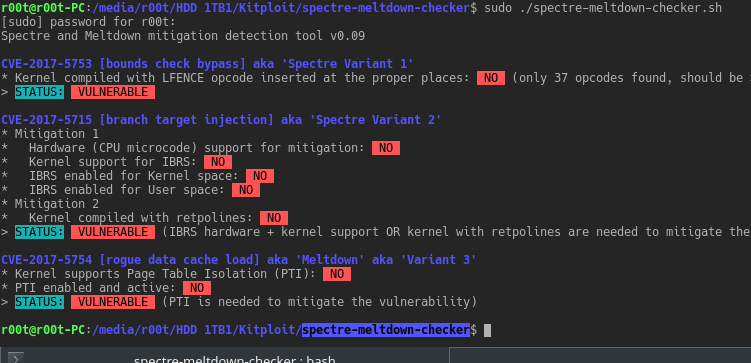
A simple shell script to tell if your Linux installation is vulnerable against the 3 “speculative execution” CVEs: CVE-2017-5753 bounds check...
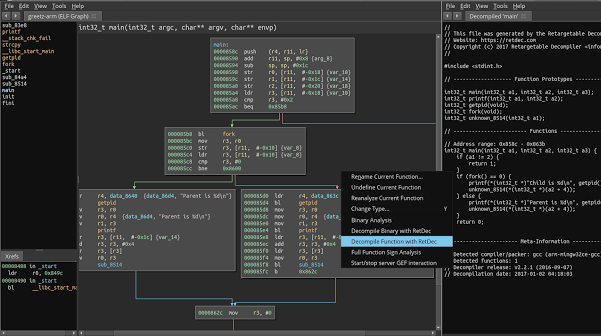
RetDec is a retargetable machine-code decompiler based on LLVM. The decompiler is not limited to any particular target architecture, operating system, or...
Defeating Google’s audio reCaptcha system with 85% accuracy. Inspiration Across the Internet, hundreds of thousands of sites rely on Google’s...
We are excited to announce this major release of auditing tool Lynis. Several big changes have been made to core functions of Lynis. These changes are the next...