[sc name=”ad_1″] Malware Source Code Collection !!! DISCLAIMER !!! We do not take any responsibility for any damage done by the code in this...
Search Results For - DDoS
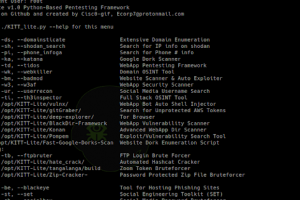
[sc name=”ad_1″] The KITT Penetration Testing Framework was developed as an open source solution for pentesters and programmers alike to compile...
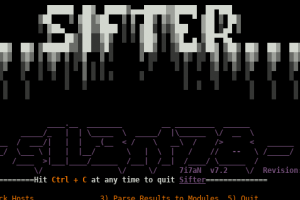
[sc name=”ad_1″] Sifter is a osint, recon & vulnerability scanner. It combines a plethara of tools within different module sets in order to...
[sc name=”ad_1″] Modern Denial-of-service ToolKit Main window Methods: Method Target Description SMS +PHONE SMS & CALL FLOOD NTP IP:PORT NTP...
[sc name=”ad_1″] Security researchers have uncovered a new variant of the infamous Mirai Internet of Things botnet, this time targeting embedded...
[sc name=”ad_1″] The world of cybersecurity is fast-paced and ever-changing. New attacks are unleashed every day, and companies around the world...
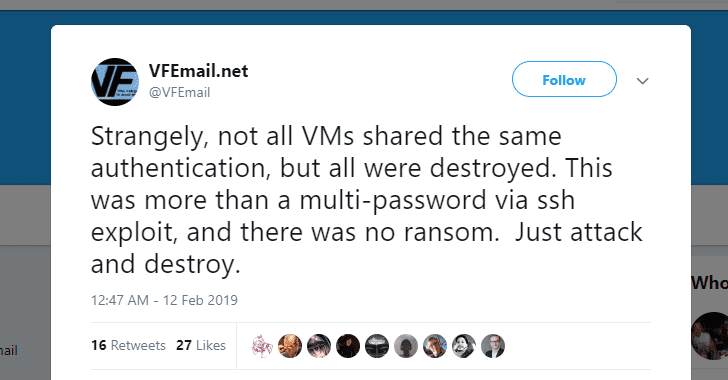
[sc name=”ad_1″] What could be more frightening than a service informing you that all your data is gone—every file and every backup servers are...
Hacking requires a lot of brainstorming since you need a robust machine that will not lag or run out of resources during working. Hacking involves DDOS a...
Mass mailer is commonly used to send a phishing page link to the e-mail ID of the target. The attacker needs to be aware of the e-mail harvester technique to...
Nmap (“Network Mapper”) is a free and open source utility for network discovery and security auditing. Many systems and network administrators also...