The CryptoShuffler malware has been discovered by security researchers from Kaspersky Lab, cybercriminals are using this malware to steal cryptocurrencies from...
Search Results For - DDE
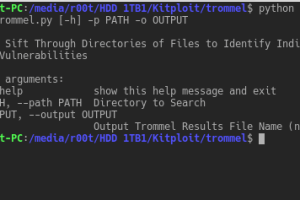
TROMMEL sifts through directories of files to identify indicators that may contain vulnerabilities. TROMMEL identifies the following indicators related to:...
We are excited to announce this major release of auditing tool Lynis. Several big changes have been made to core functions of Lynis. These changes are the next...
cve-search is a tool to import CVE (Common Vulnerabilities and Exposures) and CPE (Common Platform Enumeration) into a MongoDB to facilitate search and...
Use nmap to scan hidden “onion” services on the Tor network. Minimal image based on alpine, using proxychains to wrap nmap. Tor and dnsmasq are run as daemons...
Canvas fingerprinting relies on websites meaning able to receive data from HTML canvas details calmly. In future, Firefox users will be required to give their...
Onion Routed Cloud is a decentralized, anonymous, object storage platform owned and operated by allies in defense of human rights and opposition to censorship...
News reported in June that McAfee was amongst several Western technology organizations that had acceded in recent years to larger demands by Moscow for access...
Dr. Matthew Falder, 28, of Birmingham, England is at the center of one of the most horrific crimes law enforcement has come across on the Darknet. Falder has...
Hey Guys, In this video i show you a cool script called ZeroDoor which used for Generating Cross-Platform Backdoors. ZeroDoor: A script written lazily for...