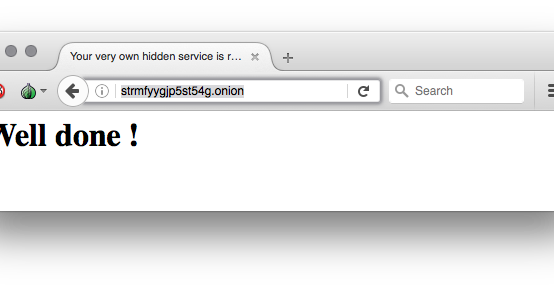
Easily run a hidden service inside the Tor network with this container Generate the skeleton configuration for you hidden service, replace for your hidden...
Search Results For - DDE
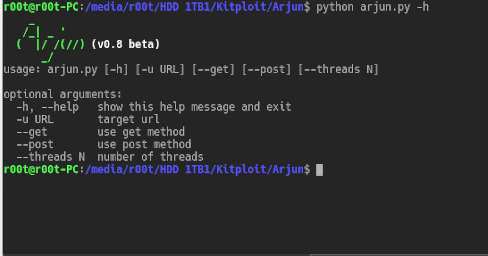
Arjun is a python script for finding hidden GET & POST parameters using regex and bruteforce. Dependencies requests threading Usages Here’s how you...
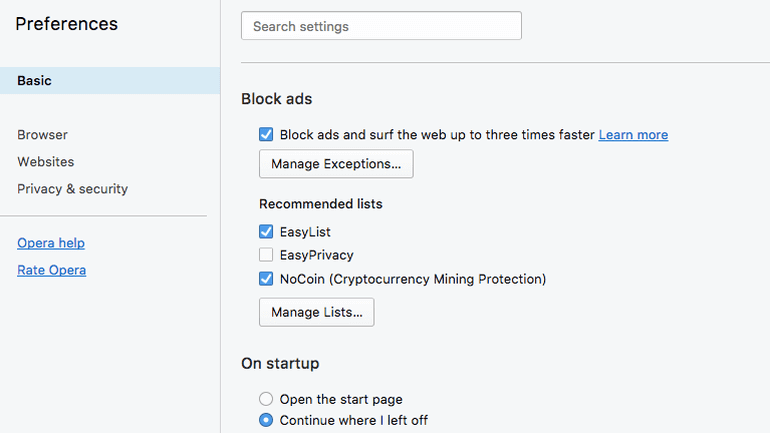
Norwegian browser maker Opera has launched the beta version of Opera 50, the first popular browser to integrate a built-in cryptocurrency-mining blocker. The...
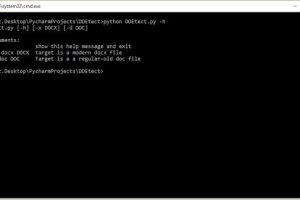
Written by Amit Serper, @0xAmit DDEtector is a simple DDE object detector written in python Currently supports only word DOCX and legacy DOC files Prints the...
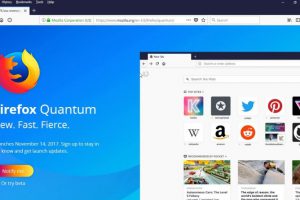
The Firefox sandboxing innovation confines the browser from the operating system in a way to block web attacks from using a vulnerability in the browser engine...
A newly discovered unpatched attacking method that exploits a built-in feature of Microsoft Office is currently being used in various widespread malware attack...
[sc name=”ad_1″] BigBountyRecon tool utilises 58 different techniques using various Google dorks and open source tools to expedite the process of...
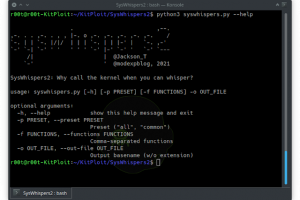
[sc name=”ad_1″] SysWhispers helps with evasion by generating header/ASM files implants can use to make direct system calls. All core syscalls are...
[sc name=”ad_1″] linux post-exploitation framework made by linux user Still under active development 中文介绍 check my blog for updates how to use what...
[sc name=”ad_1″] drow is a command-line utility that is used to inject code and hook the entrypoint of ELF executables (post-build). It takes...