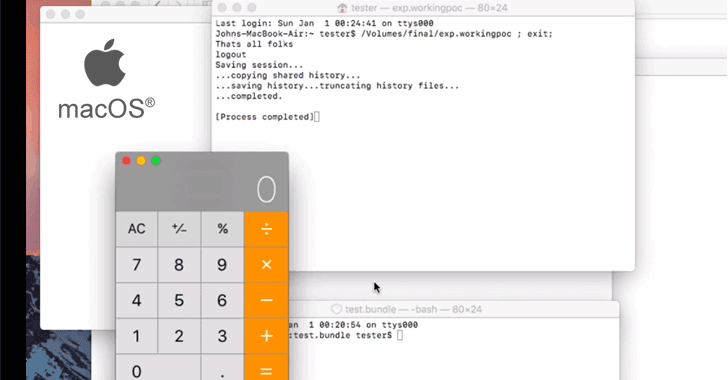
[sc name=”ad_1″] Earlier this week Dropbox team unveiled details of three critical vulnerabilities in Apple macOS operating system, which...
Search Results For - Cyber Attacks
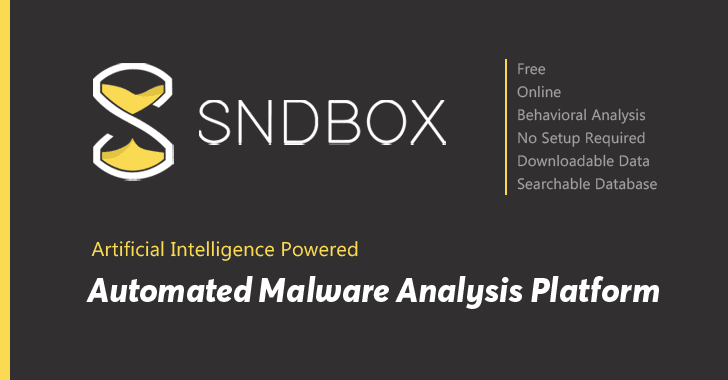
Looking for an automated malware analysis software? Something like a 1-click solution that doesn’t require any installation or configuration…a...
Pacu is an open source AWS exploitation framework, designed for offensive security testing against cloud environments. Created and maintained by Rhino Security...
In an effort to secure users’ data while maintaining privacy, Google has announced a new security measure for Android Backup Service that now encrypts...
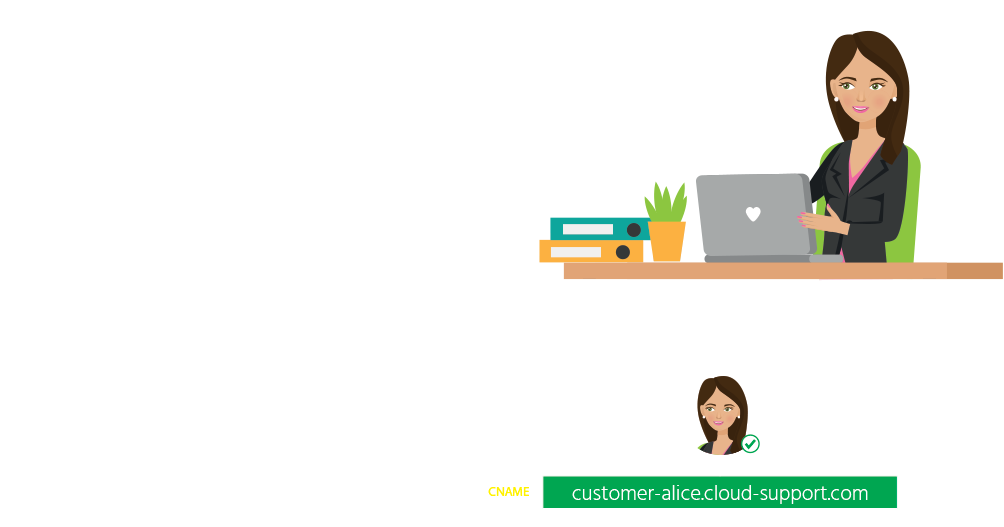
Domain Hijacking is a well-known security issue that can be carried in many different ways. In addition to social engineering or unauthorized access to the...
Hardentools is a collection of simple utilities designed to disable a number of “features” exposed by operating systems (Microsoft Windows, for now), and...
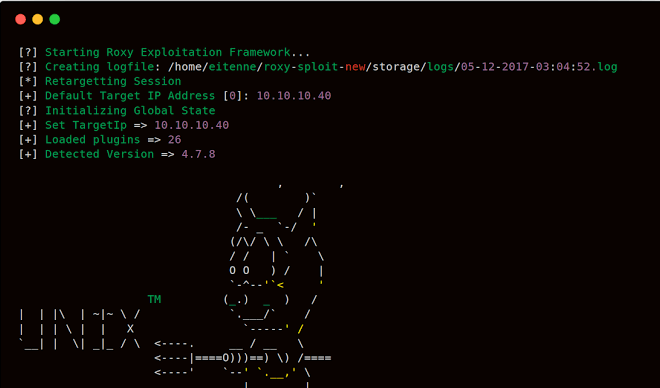
roxysploit is a community-supported, open-source and penetration testing suite that supports attacks for numerous scenarios. conducting attacks in the field...
The malicious software uncovered pornographic ads and attempted to trick users into buying added services, according to Check Point. “We’ve eliminated the apps...
Ben Wallace cited tech firms for staying happy to selling user data but not to give it to the administration which was being compelled to spend vast sums on de...
Qubes OS is a security-oriented operating system (OS). The OS is the software that runs all the other programs on a computer. Some examples of popular OSes are...