[sc name=”ad_1″] SecGen creates vulnerable virtual machines, lab environments, and hacking challenges, so students can learn security penetration...
Search Results For - Cyber Attacks
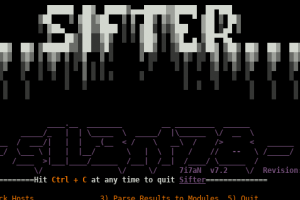
[sc name=”ad_1″] Sifter is a osint, recon & vulnerability scanner. It combines a plethara of tools within different module sets in order to...
[sc name=”ad_1″] Modern Denial-of-service ToolKit Main window Methods: Method Target Description SMS +PHONE SMS & CALL FLOOD NTP IP:PORT NTP...
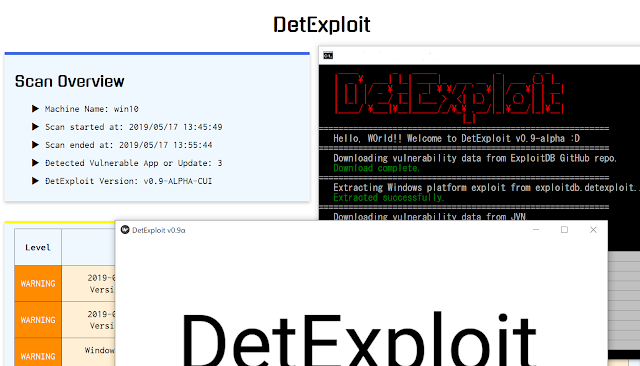
[sc name=”ad_1″] DetExploit is software that detect vulnerable applications and not-installed important OS updates on the system, and notify them...
[sc name=”ad_1″] It’s time for another batch of “Patch Tuesday” updates from Microsoft. Microsoft today released its March 2019...
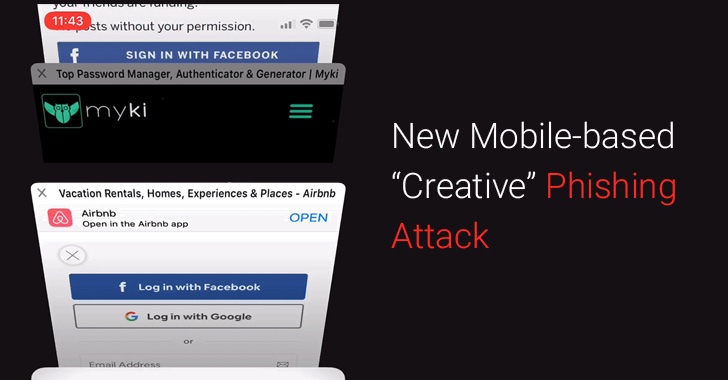
[sc name=”ad_1″] A cybersecurity researcher who last month warned of a creative phishing campaign has now shared details of a new but similar...
[sc name=”ad_1″] Cybersecurity researcher at Google’s Project Zero division has publicly disclosed details and proof-of-concept exploit of a...
[sc name=”ad_1″] The world of cybersecurity is fast-paced and ever-changing. New attacks are unleashed every day, and companies around the world...
[sc name=”ad_1″] It’s not just the critical Drupal vulnerability that is being exploited by in the wild cybercriminals to attack vulnerable...
[sc name=”ad_1″] Cybercriminals have actively started exploiting an already patched security vulnerability in the wild to install cryptocurrency...