Cryptocurrencies such as Bitcoin have been gaining more and more public attention over recent years. Now, the digital currency industry has hit Hollywood with...
Search Results For - Crypto
Despite countless examples to the contrary, many people still toss cryptocurrency and criminal activity into the same bucket. But is this born out of ignorance...
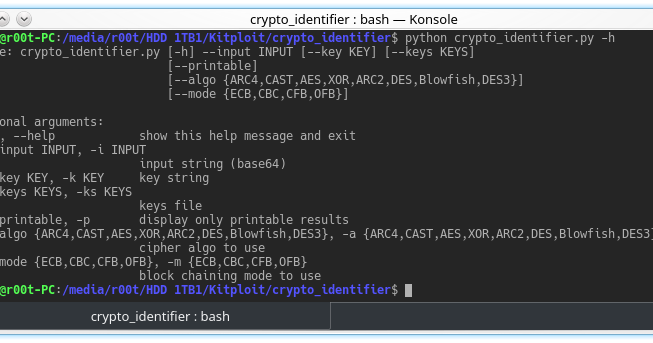
Crypto tool for pentest and ctf : try to uncipher data using multiple algorithms and block chaining modes. Usefull for a quick check on unknown cipher text and...
Many investors that want to enter the cryptocurrency market have never traded any form of a financial instrument before. Most of them, however, have some form...
Author: Cole Gibson Before it became intertwined in the controversy surrounding Facebook’s misuse of data, Cambridge Analytica was planning to raise funds for...
Author: Erin Gorsline The move marks the first time a Japanese Bank will launch a cryptocurrency and exchange. Worth more than financial mega-giant Bank of...
Collaborative (mitm) cryptocurrency mining pool in wifi networks. This script performs autonomous MITM attack on WiFi networks. It will inject a javascript in...
Quite recently, the founder of Mcafee company, John Mcafee, was in news when his Twitter was hacked by an unknown hacker. This hacker used John’s social media...
Most Android malware is at best annoying, but rarely does it cause physical damage to a phone. Not so with Loapi, a newly-discovered trojan with a...
Security researchers from Kaspersky have discovered a new malware that is targeting Android phones. This malware, called as Loapi, is a harmful piece of code...