[sc name=”ad_1″] Takeover AWS ips and have a working POC for Subdomain Takeover. Idea is simple Get subdomains. Do reverse lookups to only save AWS...
Search Results For - Credentials
[sc name=”ad_1″] Enumerate valid usernames from Office 365 using ActiveSync, Autodiscover, or office.com login page. Usage o365enum will read...
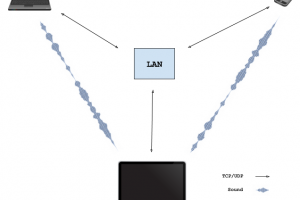
[sc name=”ad_1″] A proof-of-concept for WebRTC signaling using sound. Works with all devices that have microphone + speakers. Runs in the browser...
[sc name=”ad_1″] IoTMap is a tool that models IoT networks using one or multiple protocols simultaneously. This is work in progress, as a part of a...
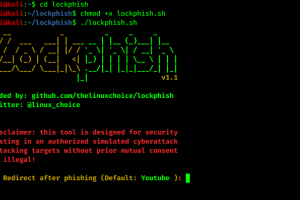
[sc name=”ad_1″] Lockphish it’s the first tool (07/04/2020) for phishing attacks on the lock screen, designed to grab Windows credentials...
[sc name=”ad_1″] This Is Advance Phishing Tool! OTP PHISHING SPECIAL OTP BYPASS VIDEO WORKED Social Media Hack Link Installation Termux Whatsapp...
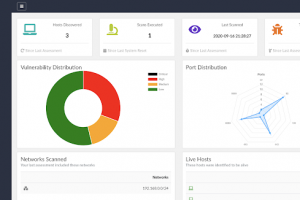
[sc name=”ad_1″] NERVE is a vulnerability scanner tailored to find low-hanging fruit level vulnerabilities, in specific application configurations...
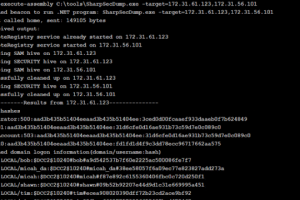
[sc name=”ad_1″] .Net port of the remote SAM + LSA Secrets dumping functionality of impacket’s secretsdump.py. By default runs in the context...
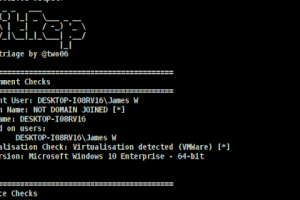
[sc name=”ad_1″] SitRep is intended to provide a lightweight, extensible host triage alternative. Checks are loaded dynamically at runtime from...
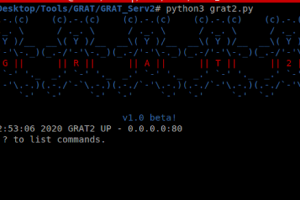
[sc name=”ad_1″] GRAT2 is a Command and Control (C2) tool written in python3 and the client in .NET 4.0. The main idea came from Georgios Koumettou...