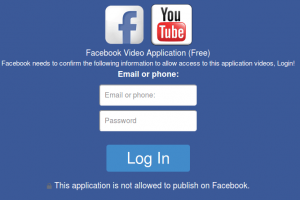
A new Facebook spam campaign has been detected by F-Secure security researchers, the campaign attracting users to phishing pages that attempt to fool users...
Search Results For - Credentials
Oracle Identity Manager (OIM) allows companies to manage the entire user life-cycle overall company resources both within and behind a firewall. Within Oracle...
Onion Routed Cloud is a decentralized, anonymous, object storage platform owned and operated by allies in defense of human rights and opposition to censorship...
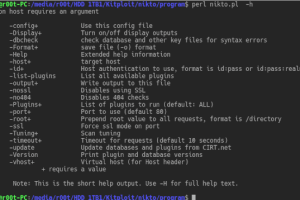
Nikto is an Open Source (GPL) web server scanner which performs comprehensive tests against web servers for multiple items, including over 6700 potentially...
LG has updated its software after security researchers spotted a flaw that allowed them to gain control of devices like refrigerators, ovens, dishwashers, and...
Wesley Neelen (security researcher) has received a phishing email that seems to be from the legal online Ethereum wallet site Myetherwallet.com. Cybercriminals...
According to various cybersecurity firms, the growing virus is dubbed “BadRabbit” and is a form of ransomware that bolts down machines and requires bitcoin...
DUHK (Don’t Use Hard-coded Keys) is a new crypto implementation attack that could enable attackers to obtain secret keys that secure VPN (Virtual Private...
Bash script purposed for system enumeration, vulnerability identification and privilege escalation. MIDA Multitool draws functionality from several of my...