Palihapitiya’s judgments were directed not only at Facebook but the broader online ecosystem. “The short-term, dopamine-driven feedback circles we’ve produced...
Search Results For - Control
On December 14, the company will vote to repeal the net neutrality practices it put in place in 2015. With Republicans agents who oppose the rules outnumbering...
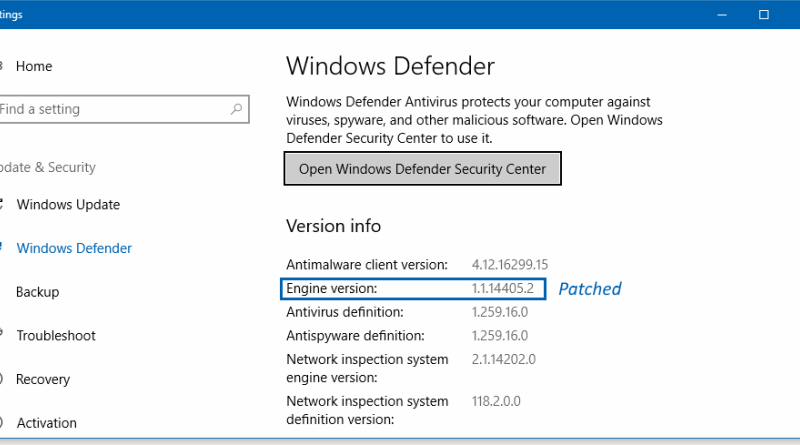
On Wednesday, Microsoft has released a patch for the Microsoft Malware Protection Engine (MPE) to fix a critical severity remote code execution (RCE) flaw in...
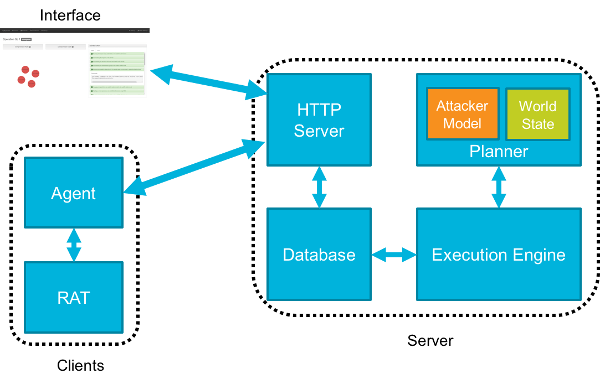
CALDERA is an automated adversary emulation system that performs post-compromise adversarial behavior within enterprise networks. It generates plans during...
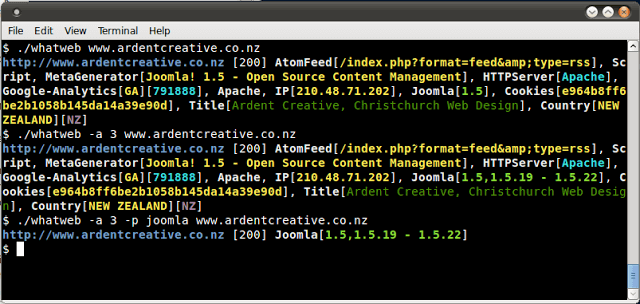
WhatWeb identifies websites. Its goal is to answer the question, “What is that Website?”. WhatWeb recognises web technologies including content management...
After rapidly reinforcing a flaw that acknowledged anyone with access to a High Sierra Mac to take administrative control, Apple still has extra work to do to...
The group, called Google You Owe Us, said in a declaration Thursday that it was the first case of its sort in the U.K. against a major tech business over the...
sslh accepts connections on specified ports, and forwards them further based on tests performed on the first data packet sent by the remote client. Probes for...
DBC2 (DropboxC2) is a modular post-exploitation tool, composed of an agent running on the victim’s machine, a controler, running on any machine...
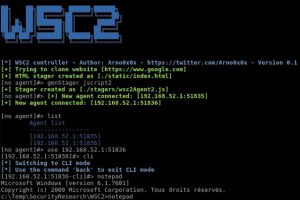
WSC2 is a PoC of using the WebSockets and a browser process to serve as a C2 communication channel between an agent, running on the target system, and a...