Snowden told Moudeina that he was operating on an app that could turn a mobile device into a kind of motion sensor in form to notify you when your things are...
Search Results For - Control
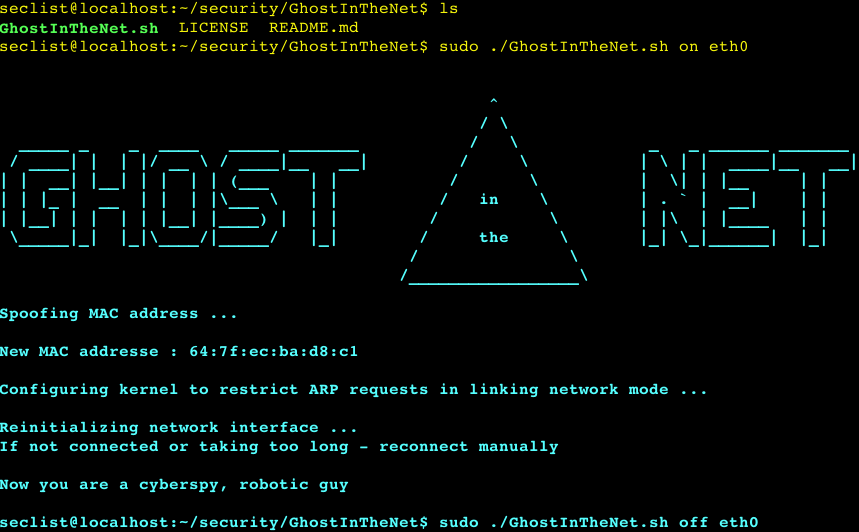
Ultimate Network Stealther that makes Linux a Ghost In The Net and protects from MITM/DOS/scan. Properties: Network Invisibility Network Anonymity Protects...
RetDec is a retargetable machine-code decompiler based on LLVM. The decompiler is not limited to any particular target architecture, operating system, or...
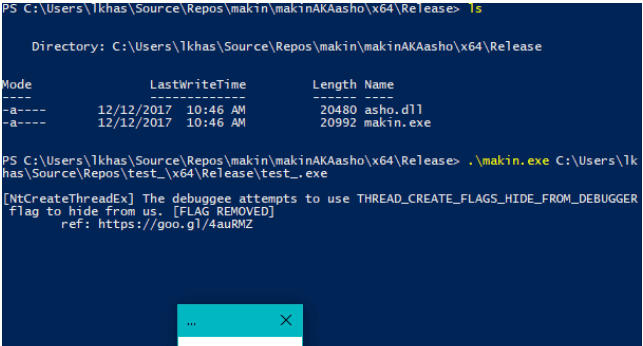
makin is to make initial malware assessment little bit easier, It helps to reveal a debugger detection techniques used by a sample. Supports x64 and x86 How...
Recently, Triconex Industries was put at risk when hackers attempted to hack into its security systems, trying to control things. These attacks have a pattern...
ADRecon is a tool which extracts various artifacts (as highlighted below) out of an AD environment in a specially formatted Microsoft Excel report that...
Wifiphisher is a security tool that mounts automated victim-customized phishing attacks against WiFi clients in order to obtain credentials or infect the...
Before you throw your computer into a lake, rest ensured this ain’t over. In the days, weeks, and periods to follow honestly, indeed in the next few hours the...
Tiredful API is intentionally designed broken app. The aim of this web app is to teach developers, QA or security professionals about flaws present in...
The maker of a sneaky adware that hijacks a user’s browser to serve ads is back with a new, more advanced version — one that can gain root...