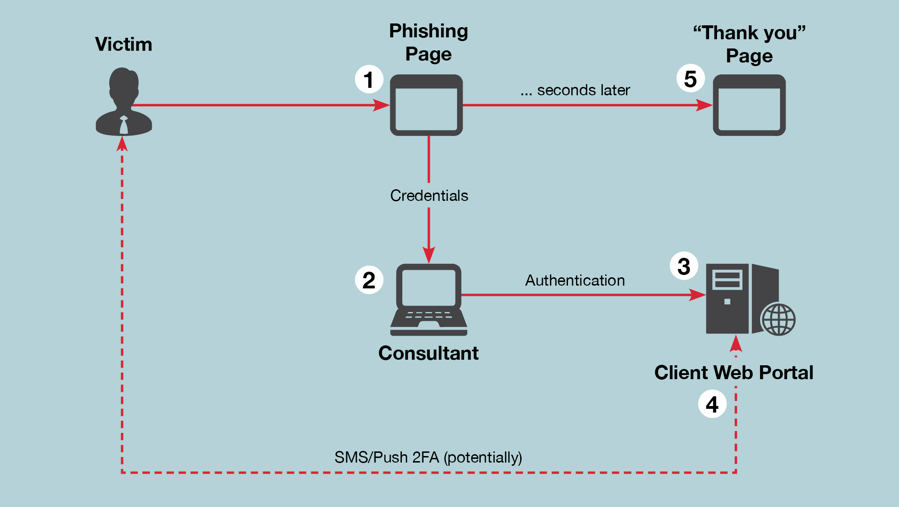
ReelPhish simplifies the real-time phishing technique. The primary component of the phishing tool is designed to be run on the attacker’s system. It consists...
Search Results For - Control
roxysploit is a community-supported, open-source and penetration testing suite that supports attacks for numerous scenarios. conducting attacks in the field...
Grouper is a slightly wobbly PowerShell module designed for pentesters and redteamers (although probably also useful for sysadmins) which sifts through the...
Evilgrade is a modular framework that allows the user to take advantage of poor upgrade implementations by injecting fake updates. It comes with pre-made...
The Nmap Scanner for Telco. With the current focus on telecom security, there used tools in day to day IT side penetration testing should be extended to...
SDRtrunk is an integrated application for demodulating radio signals and decoding trunked radio network protocols and some related radio signal formats. The...
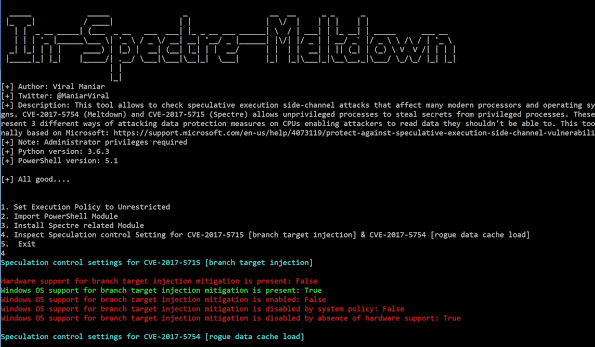
This tool allows to check speculative execution side-channel attacks that affect many modern processors and operating systems designs. CVE-2017-5754 (Meltdown)...
Wapiti allows you to audit the security of your websites or web applications. It performs “black-box” scans (it does not study the source code) of...
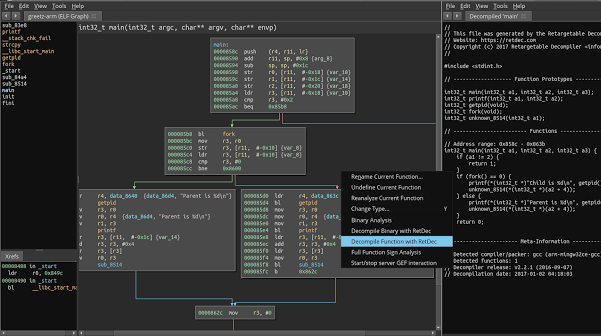
RetDec is a retargetable machine-code decompiler based on LLVM. The decompiler is not limited to any particular target architecture, operating system, or...
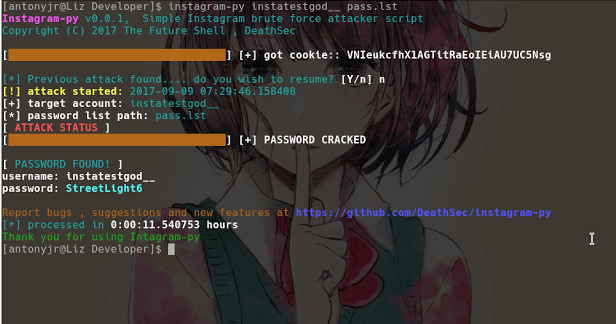
Instagram-Py is a simple python script to perform basic brute force attack against Instagram , this script can bypass login limiting on wrong passwords , so...