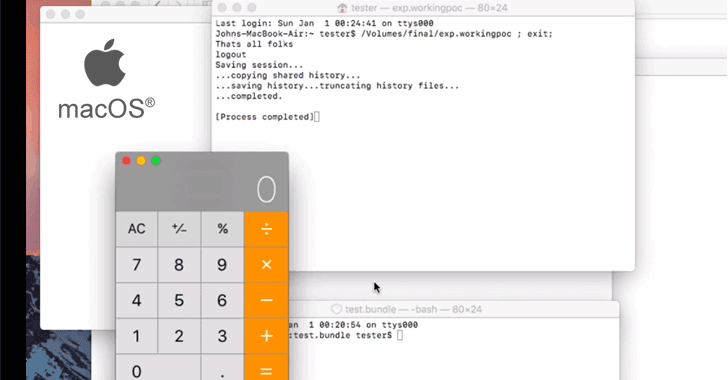
[sc name=”ad_1″] Earlier this week Dropbox team unveiled details of three critical vulnerabilities in Apple macOS operating system, which...
Search Results For - Control
[sc name=”ad_1″] This may sound crazy, but it’s true! The war for “most-subscribed Youtube channel” crown between T-Series and...
[sc name=”ad_1″] Cybersecurity researchers have discovered a new zero-day vulnerability in Adobe Flash Player that hackers are actively exploiting...
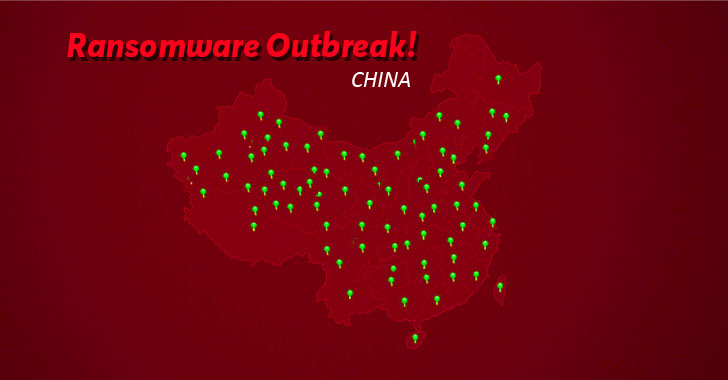
A new piece of ransomware is spreading rapidly across China that has already infected more than 100,000 computers in the last four days as a result of a supply...
Looking for an automated malware analysis software? Something like a 1-click solution that doesn’t require any installation or configuration…a...
AutoRDPwn is a script created in Powershell and designed to automate the Shadow attack on Microsoft Windows computers. This vulnerability allows a remote...
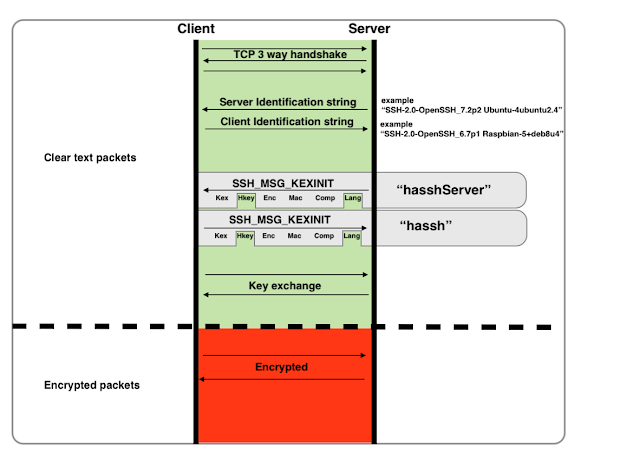
“HASSH” is a network fingerprinting standard which can be used to identify specific Client and Server SSH implementations. The fingerprints can be...
novahot is a webshell framework for penetration testers. It implements a JSON-based API that can communicate with trojans written in any language. By default...
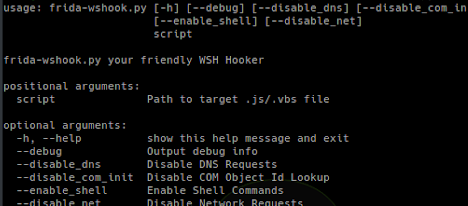
frida-wshook is an analysis and instrumentation tool which uses frida.re to hook common functions often used by malicious script files which are run using...
A 21-year-old Kentucky man who previously pleaded guilty to developing, marketing, and selling an infamous remote access trojan (RAT) called LuminosityLink has...